Security News

The FBI has recently published a new public services announcement, warning again about the continuous evolution and danger of BEC attacks. Attack chain from AiTM phishing attack to BEC. This particular attack started with a phishing email from one of the target organizations' trusted vendors, instructing the target to view or download a fax document.

As it evolves into a critical component of threat and exposure management strategies, it's worth examining why attack surface management has grown to become a key category, and why it will continue to be a necessity for organizations worldwide. The attack surface includes any IT asset connected to the internet - applications, IoT devices, Kubernetes clusters, cloud platforms - that threat actors could infiltrate and exploit to perpetuate an attack.

British Airways, BBC and Boots have all been served an ultimatum after they were hit with a supply-chain attack by the ransomware group Clop. In February 2023, Clop claimed responsibility for a supply-chain attack that affected more than 130 organizations, including data belonging to CHS Healthcare patients.
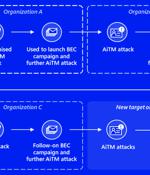
Banking and financial services organizations are the targets of a new multi-stage adversary-in-the-middle phishing and business email compromise attack, Microsoft has revealed. "The attack originated from a compromised trusted vendor and transitioned into a series of AiTM attacks and follow-on BEC activity spanning multiple organizations," the tech giant disclosed in a Thursday report.

The Microsoft Azure Portal is down on the web as a threat actor known as Anonymous Suda claims to be targeting the site with a DDoS attack.At the same time, a threat actor known as Anonymous Sudan claims to be conducting a DDoS attack against the Microsoft Azure portal, sharing an image of the page not working.

A new custom backdoor dubbed Stealth Soldier has been deployed as part of a set of highly-targeted espionage attacks in North Africa. "Stealth Soldier malware is an undocumented backdoor that primarily operates surveillance functions such as file exfiltration, screen and microphone recording, keystroke logging and stealing browser information," cybersecurity company Check Point said in a technical report.

Researchers have released a proof-of-concept exploit for an actively exploited Windows local privilege escalation vulnerability fixed as part of the May 2023 Patch Tuesday. To raise awareness about the actively exploited flaw, and the need to apply Windows security updates, CISA also published an alert and added it to its "Known Exploited Vulnerabilities" catalog.

Microsoft is investigating an ongoing outage that is preventing OneDrive customers from accessing the cloud file hosting service worldwide, just as a threat actor known as 'Anonymous Sudan' claims to be DDoSing the service. "We've reviewing OneDrive telemetry that captures this impact scenario to determine the source of the service access failures and begin identifying a mitigation plan."

Pharmaceutical company Eisai has disclosed it suffered a ransomware incident that impacted its operations, admitting that attackers encrypted some of its servers. Eisai is a Tokyo-based pharmaceutical company with an annual revenue of $5.3 billion and over 10,000 employees.

The North Korean nation-state threat actor known as Kimsuky has been linked to a social engineering campaign targeting experts in North Korean affairs with the goal of stealing Google credentials and delivering reconnaissance malware. "Further, Kimsuky's objective extends to the theft of subscription credentials from NK News," cybersecurity firm SentinelOne said in a report shared with The Hacker News.