Security News

Multiple security vulnerabilities have been disclosed in the Exim mail transfer agent that, if successfully exploited, could result in information disclosure and remote code execution. The list of...

A critical zero-day vulnerability in all versions of Exim mail transfer agent software can let unauthenticated attackers gain remote code execution on Internet-exposed servers. MTA servers like Exim are highly vulnerable targets, primarily because they are often accessible via the Internet, serving as easy entry points for attackers into a target's network.

Google and Mozilla have patched a zero-day exploit in Chrome and Firefox, respectively. The zero-day exploit could leave users open to a heap buffer overflow, through which attackers could inject malicious code.

The FBI has warned about a new trend in ransomware attacks where multiple strains are deployed on victims' networks to encrypt systems in under two days. Variants used in these dual ransomware attacks include AvosLocker, Diamond, Hive, Karakurt, LockBit, Quantum, and Royal.

Cisco warned customers on Wednesday to patch a zero-day IOS and IOS XE software vulnerability targeted by attackers in the wild."An attacker could exploit this vulnerability by either compromising an installed key server or modifying the configuration of a group member to point to a key server that is controlled by the attacker," Cisco explained in a security advisory published on Wednesday.

In 2023, a wave of new attacks targeting Kubernetes has been reported, from Dero and Monero crypto mining to Scarleteel and RBAC-Buster. In this Help Net Security video, Jimmy Mesta, CTO at KSOC, explores what it would take to protect against Kubernetes attacks in the real world.

Johnson Controls International has suffered what is described as a massive ransomware attack that encrypted many of the company devices, including VMware ESXi servers, impacting the company's and its subsidiaries' operations.Yesterday, a source told BleepingComputer that Johnson Controls suffered a ransomware attack after initially being breached at its Asia offices.
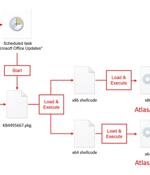
A new threat actor known as AtlasCross has been observed leveraging Red Cross-themed phishing lures to deliver two previously undocumented backdoors named DangerAds and AtlasAgent. NSFOCUS...

Researchers from four American universities have developed a new GPU side-channel attack that leverages data compression to leak sensitive visual data from modern graphics cards when visiting web pages. The GPU.zip researchers explain that all modern graphic processor units, especially integrated Intel and AMD chips, perform software-visible data compression even when not explicitly asked.

In a paper titled, "Everlasting ROBOT: the Marvin Attack," Hubert Kario, senior quality engineer on the QE BaseOS Security team at Red Hat, shows that many software implementations of the PKCS#1 v1.5 padding scheme for RSA key exchange that were previously deemed immune to Daniel Bleichenbacher's widely known attack are vulnerable. "For TLS hosts that use forward secure ciphersuites, the attacker would have to perform a massively parallel attack to forge a server signature before a client would time out during the connection attempt. That makes the attack hard, but not impossible."