Security News

ESET investigated suspicious activity on the network of a trade group in the United States that operates in the financial sector. While helping the affected entity remediate the compromise, they...

A suspected China-based threat actor has been linked to a series of cyber attacks targeting high-profile organizations in Southeast Asia since at least October 2023. The espionage campaign...

ESET researchers have discovered a series of attacks that took place in Europe from May 2022 to March 2024, where the attackers used a toolset capable of targeting air-gapped systems, in a...

ESET researchers discovered a remote code execution vulnerability in WPS Office for Windows (CVE-2024-7262). APT-C-60, a South Korea-aligned cyberespionage group, was exploiting it to target East...

A previously undocumented advanced persistent threat group dubbed CloudSorcerer has been observed targeting Russian government entities by leveraging cloud services for command-and-control and data exfiltration. "It's a sophisticated cyber espionage tool used for stealth monitoring, data collection, and exfiltration via Microsoft Graph, Yandex Cloud, and Dropbox cloud infrastructure," the Russian security vendor said.

Governmental entities in the Middle East, Africa, and Asia are the target of a Chinese advanced persistent threat (APT) group as part of an ongoing cyber espionage campaign dubbed Operation...

Two China-linked advanced persistent threat (APT) groups have been observed targeting entities and member countries affiliated with the Association of Southeast Asian Nations (ASEAN) as part of a...

A financial entity in Vietnam was the target of a previously undocumented threat actor called Lotus Bane that was first detected in March 2023. Singapore-headquartered Group-IB described the...
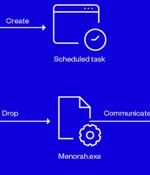
Sophisticated cyber actors backed by Iran known as OilRig have been linked to a spear-phishing campaign that infects victims with a new strain of malware called Menorah. "The malware was designed...
The threat actor known as Dark Pink has been linked to five new attacks aimed at various entities in Belgium, Brunei, Indonesia, Thailand, and Vietnam between February 2022 and April 2023. Dark Pink, also called Saaiwc Group, is an advanced persistent threat actor believed to be of Asia-Pacific origin, with attacks targeting entities primarily located in East Asia and, to a lesser extent, in Europe.