Security News
Researchers at cybersecurity research and consulting firm Trail of Bits have discovered a vulnerability that could allow attackers to read GPU local memory from affected Apple, Qualcomm, AMD and Imagination GPUs. In particular, the vulnerability-which the researchers named LeftoverLocals-can access conversations performed with large language models and machine learning models on affected GPUs.
Researchers at cybersecurity research and consulting firm Trail of Bits have discovered a vulnerability that could allow attackers to read GPU local memory from affected Apple, Qualcomm, AMD and Imagination GPUs. In particular, the vulnerability-which the researchers named LeftoverLocals-can access conversations performed with large language models and machine learning models on affected GPUs.

Research made public on Tuesday detailed how miscreants can exploit the hole to read data they're not supposed to in a system's local GPU memory. While the flaw potentially affects all GPU applications on vulnerable chips, it is especially concerning for those processing machine-learning applications because of the amount of data these models process using GPUs, and therefore the amount of potentially sensitive information that could be swiped by exploiting this issue.

A new vulnerability dubbed 'LeftoverLocals' affecting graphics processing units from AMD, Apple, Qualcomm, and Imagination Technologies allows retrieving data from the local memory space. [...]

Protestors reportedly used AirDrop to share anti-government material during China's long and strict COVID-19 lockdowns. Which is why Chinese authorities last week admitted that the use of AirDrop is considered problematic after police previously found inappropriate material being shared on the Beijing subway using the protocol.

The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has added six security flaws to its Known Exploited Vulnerabilities (KEV) catalog, citing evidence of active exploitation. This...

A Chinese state-backed research institute claims to have discovered how to decrypt device logs for Apple's AirDrop feature, allowing the government to identify phone numbers or email addresses of those who shared content. China has a long history of censoring its people, requesting Apple block access to mobile apps, blocking encrypted messaging apps, such as Signal, and creating the Great Firewall of China to control what sites can be visited in the country.
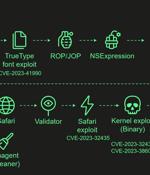
The Operation Triangulation spyware attacks targeting Apple iOS devices leveraged never-before-seen exploits that made it possible to even bypass pivotal hardware-based security protections...

Apple on Monday released security patches for iOS, iPadOS, macOS, tvOS, watchOS, and Safari web browser to address multiple security flaws, in addition to backporting fixes for two recently...

Apple has issued emergency security updates to backport patches for two actively exploited zero-day flaws to older iPhones and some Apple Watch and Apple TV models. Today, Apple addressed the zero-days in iOS 16.7.3, iPadOS 16.7.3, tvOS 17.2, and watchOS 10.2 with improved input validation and locking.