Security News

T-Mobile disclosed a new data breach after a threat actor stole the personal information of 37 million current postpaid and prepaid customer accounts through one of its Application Programming...
Multiple bugs affecting millions of vehicles from 16 different manufacturers could be abused to unlock, start, and track cars, plus impact the privacy of car owners. The research builds on earlier findings from late last year, when Yuga Labs researcher Sam Curry et al detailed security flaws in a connected vehicle service provided by SiriusXM that could potentially put cars at risk of remote attacks.

At a surface level, APIs help businesses to connect applications and share data with one another. The recent push to focus on API security comes at a critical time where more enterprises are relying on enterprise mobility, meaning increasing a reliance on mobile app connectivity.

Inadequate security testing and a lack of business logic have resulted in an overall rise in API security risks. The API threats to eCommerce security are potentially devastating to retailers and customers.

The transformation comes as 68% of respondents cite their fears about API sprawl. Ensuring data security and controlling API sprawl were top concerns, with 68% worrying about complexity due to sprawl and 48% of respondents ranking "Increased security challenges" as their single greatest concern with API growth.

You will also receive a complimentary subscription to TechRepublic's News and Special Offers newsletter and the Top Story of the Day newsletter. You may unsubscribe from these newsletters at any time.

Researchers discovered 1,550 mobile apps leaking Algolia API keys, risking the exposure of sensitive internal services and stored user information. Of those keys, only the Search is meant to be public and available on front-end code, helping users perform search queries on the apps.

In this Help Net Security video, Dr. Pedram Hayati, Founder of SecDim, offers a technical write-up based on a secure programming challenge. The task was inspired by a major security breach that happened to a telco in Australia and offers lessons learned when it comes to hardening public API REST endpoints.
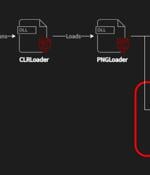
A recently discovered cyber espionage group dubbed Worok has been found hiding malware in seemingly innocuous image files, corroborating a crucial link in the threat actor's infection chain. Czech cybersecurity firm Avast said the purpose of the PNG files is to conceal a payload that's used to facilitate information theft.

A range of automated threats - from account takeover, credit card fraud, web scraping, API abuses, Grinch bots, and distributed denial of service attacks - were a persistent challenge for the eCommerce industry, threatening online sales and customer satisfaction. "This industry faces a variety of security risks, the majority of which are automated and operate around the clock. Retailers need a unified approach to stop these persistent attacks, one that focuses on the protection of data and is equipped to mitigate attacks quickly without disrupting shoppers."