Security News

A new security flaw has been addressed in the Apache OFBiz open-source enterprise resource planning (ERP) system that, if successfully exploited, could lead to unauthenticated remote code...

Apache has fixed a critical security vulnerability in its open-source OFBiz (Open For Business) software, which could allow attackers to execute arbitrary code on vulnerable Linux and Windows...

The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Tuesday added a critical security flaw affecting the Apache OFBiz open-source enterprise resource planning (ERP) system to its...

The U.S. Cybersecurity & Infrastructure Security Agency is warning of two vulnerabilities exploited in attacks, including a path traversal impacting Apache OFBiz. [...]
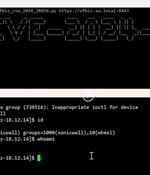
A new zero-day pre-authentication remote code execution vulnerability has been disclosed in the Apache OFBiz open-source enterprise resource planning system that could allow threat actors to achieve remote code execution on affected instances. "The root cause of the vulnerability lies in a flaw in the authentication mechanism," SonicWall, which discovered and reported the shortcoming, said in a statement.

CVE-2024-38856, an incorrect authorization vulnerability affecting all but the latest version of Apache OFBiz, may be exploited by remote, unauthenticated attackers to execute arbitrary code on vulnerable systems. Apache OFBiz is an open-source framework for enterprise resource planning that encompasses web applications that serve common business needs, such as human resources, accounting, inventory management, customer relationship management, marketing and so on.

Threat actors are actively exploiting a recently disclosed critical security flaw impacting Apache HugeGraph-Server that could lead to remote code execution attacks. It has been described as a remote command execution flaw in the Gremlin graph traversal language API. "Users are recommended to upgrade to version 1.3.0 with Java11 and enable the Auth system, which fixes the issue," the Apache Software Foundation noted in late April 2024.

Your profile can be used to present content that appears more relevant based on your possible interests, such as by adapting the order in which content is shown to you, so that it is even easier for you to find content that matches your interests. Content presented to you on this service can be based on your content personalisation profiles, which can reflect your activity on this or other services, possible interests and personal aspects.

The distributed denial-of-service (DDoS) botnet known as Muhstik has been observed leveraging a now-patched security flaw impacting Apache RocketMQ to co-opt susceptible servers and expand its...

Your profile can be used to present content that appears more relevant based on your possible interests, such as by adapting the order in which content is shown to you, so that it is even easier for you to find content that matches your interests. Content presented to you on this service can be based on your content personalisation profiles, which can reflect your activity on this or other services, possible interests and personal aspects.