Security News

Google plans to extend its rework of web ad technology - the optimistically named Privacy Sandbox - to Android devices in an effort to limit the misuse of data in its mobile ecosystem. It began to take shape a year after Google undertook Project Strobe, a rethink of Google Account and Android data access in the wake of ongoing security and privacy problems.
The public preview for the Android apps for Windows 11 is now live in the US, allowing users to run Android apps natively on the Windows desktop. The feature relies on a new platform called Windows Subsystem for Android that runs Android apps in a virtual machine to provide compatibility with the Android Open Source Project and hardware input devices.

The February edition of Google's monthly Android security update tackles, among other vulnerabilities, an eyebrow-raising critical flaw in Android 12. This February security patch batch marks the final official update for Google's Pixel 3 smartphones, which launched in October 2018, which is like a century ago for the internet goliath.

Google has released the February 2022 Android security updates, addressing two critical vulnerabilities, one being a remote escalation of privilege that requires no user interaction. The vulnerability is tracked as CVE-2021-39675, carrying a "Critical" severity rating, and affects only Android 12, the latest version of the popular OS. These flaws are typically leveraged by sophisticated spyware vendors that independently discover and privately use zero-days in mobile operating systems.

A financially motivated campaign that targets Android devices and spreads mobile malware via SMS phishing techniques since at least 2018 has spread its tentacles to strike victims located in France and Germany for the first time. Dubbed Roaming Mantis, the latest spate of activities observed in 2021 involve sending fake shipping-related texts containing a URL to a landing page from where Android users are infected with a banking trojan known as Wroba whereas iPhone users are redirected to a phishing page that masquerades as the official Apple website.
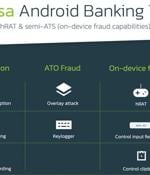
Two different Android banking Trojans, FluBot and Medusa, are relying on the same delivery vehicle as part of a simultaneous attack campaign, according to new research published by ThreatFabric. The ongoing side-by-side infections, facilitated through the same smishing infrastructure, involved the overlapping usage of "App names, package names, and similar icons," the Dutch mobile security firm said.

Flubot, the Android spyware that's been spreading virally since last year, has hitched its infrastructure wagon up to another mobile threat known as Medusa. That's according to ThreatFabric, which found that Medusa is now being distributed through the same SMS-phishing infrastructure as Flubot, resulting in high-volume, side-by-side campaigns.

The Roaming Mantis Android malware campaign has buzzed into Europe, quickly infesting France in particular, where there have been 66,789 downloads of the group's specific remote access trojan as of January. The campaign pushes the Android RAT known as Wroba onto victim devices.

The Medusa Android banking Trojan is seeing increased infection rates as it targets more geographic regions to steal online credentials and perform financial fraud. Today, researchers at ThreatFabric have published a new report detailing the latest tricks employed by the Medusa malware and how it continues to evolve with new features.

The Roaming Mantis SMS phishing campaign has finally reached Europe, as researchers detect campaigns targeting Android and iPhone users in Germany and France with malicious apps and phishing pages. Roaming Mantis is a credential theft and malware distribution campaign that uses SMS phishing to distribute malicious Android apps as standalone APK files outside the Google Play Store.