Security News

A malicious Android app that steals Facebook credentials has been installed over 100,000 times via the Google Play Store, with the app still available to download. The Android malware is disguised as a cartoonifier app called 'Craftsart Cartoon Photo Tools,' allowing users to upload an image and convert it into a cartoon rendering. Over the past week, security researchers and mobile security firm Pradeo discovered that the Android app includes a trojan called 'FaceStealer,' which displays a Facebook login screen that requires users to log in before using the app.

Security researchers tracking the mobile app ecosystem have noticed a recent spike in trojan infiltration on the Google Play Store, with one of the apps having over 500,000 installs and available to download. Most of these apps belong to a family of trojan malware used in various scams, resulting in financial losses and also loss of sensitive personal information. The threats discovered on the Play Store by Dr. Web's analysts include cryptocurrency management apps, social benefit aid tools, Gasprom investment clones, photo editors, and a launcher themed after iOS 15.

Mobile security company Zimperium has released its annual mobile threat report where security trends and discoveries in the year that passed lay the groundwork for predicting what's coming in 2022. In 2021, actors focused more on remote workforce or on-premise mobile devices, leading to increased malicious network scans and man-in-the-middle attacks.

The Aberebot Android banking trojan has returned under the name 'Escobar' with new features, including stealing Google Authenticator multi-factor authentication codes. The malware author is renting the beta version of the malware for $3,000 per month to a maximum of five customers, with threat actors having the ability to test the bot for free for three days.

Microsoft has confirmed a new known issue causing Microsoft Intune enrollment problems on some Android devices after upgrading from Android 11 to Android 12. "Currently, this includes some OPPO, OnePlus, and Realme devices enrolled as Android Enterprise personally-owned work profile," the Intune Support Team explained.

Google is rolling out an air raid alert system to all Android phones in Ukraine to help them get back to safety from incoming Russian airstrikes. As Walker further explained, the airstrike warning system rolling out to Ukrainians' Android phones "Is supplemental to the country's existing air raid alert systems" and uses air raid alert info provided by the Ukrainian government.

Google has released the March 2022 security updates for Android 10, 11, and 12, addressing three critical severity flaws, one of which affects all devices running the latest version of the mobile OS. Tracked as CVE-2021-39708, the flaw lies in the Android System component, and it's an escalation of privilege problem requiring no user interaction or additional execution privileges. "The most severe of these issues is a critical security vulnerability in the System component that could lead to remote escalation of privilege with no additional execution privileges needed. User interaction is not needed for exploitation." - mentions Google's bulletin.

How to check Android 12 permissions with the Privacy Dashboard. One of the new features in Android 12 makes it very easy to check up on your device privacy by way of service access.
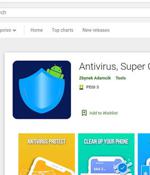
The threat actor behind a nascent Android banking trojan named SharkBot has managed to evade Google Play Store security barriers by masquerading as an antivirus app. Where SharkBot stands apart is in its ability to carry out the unauthorized transactions via Automatic Transfer Systems, which stands in contrast to TeaBot, which requires a live operator to interact with the infected devices to conduct the malicious activities.
An Android banking trojan designed to steal credentials and SMS messages has been observed sneaking past Google Play Store protections to target users of more than 400 banking and financial apps from Russia, China, and the U.S. "TeaBot RAT capabilities are achieved via the device screen's live streaming plus the abuse of Accessibility Services for remote interaction and key-logging," Cleafy researchers said in a report. Also known by the name Anatsa, TeaBot first emerged in May 2021, camouflaging its malicious functions by posing as seemingly innocuous PDF document and QR code scanner apps that are distributed via the official Google Play Store instead of third-party apps stores or via fraudulent websites.