Security News

An enterprise-grade surveillanceware dubbed Hermit has been put to use by entities operating from within Kazakhstan, Syria, and Italy over the years since 2019, new research has revealed. Lookout attributed the spy software, which is equipped to target both Android and iOS, to an Italian company named RCS Lab S.p.

Cybersecurity researchers have discovered a new Android banking malware named MaliBot, which poses as a cryptocurrency mining app or the Chrome web browser to target users in Italy and Spain. MaliBot focuses on stealing financial information such as e-banking service credentials, crypto wallet passwords, and personal details, while it's also capable of snatching two-factor authentication codes from notifications.

A new strain of Android malware has been spotted in the wild targeting online banking and cryptocurrency wallet customers in Spain and Italy, just weeks after a coordinated law enforcement operation dismantled FluBot. The information stealing trojan, codenamed MaliBot by F5 Labs, is as feature-rich as its counterparts, allowing it to steal credentials and cookies, bypass multi-factor authentication codes, and abuse Android's Accessibility Service to monitor the victim's device screen.

Cybersecurity researchers have discovered adware and information-stealing malware on the Google Play Store last month, with at least five still available and having amassed over two million downloads. Analysts at Dr. Web antivirus report that adware apps and data-stealing Trojans were among the most prominent Android threats in May 2022.
A technically sophisticated threat actor known as SeaFlower has been targeting Android and iOS users as part of an extensive campaign that mimics official cryptocurrency wallet websites intending to distribute backdoored apps that drain victims' funds. "As of today, the main current objective of SeaFlower is to modify Web3 wallets with backdoor code that ultimately exfiltrates the seed phrase," Confiant's Taha Karim said in a technical deep-dive of the campaign.

Google has released the June 2022 security updates for Android devices running OS versions 10, 11, and 12, fixing 41 vulnerabilities, five rated critical. The security update is separated into two levels, released on June 1 and June 5.

Security researchers are warning of an Android malware named SMSFactory that adds unwanted costs to the phone bill by subscribing victims to premium services. The number of its victims is unclear but attempts to infect Android devices have been recorded for tens of thousands of Android users protected by Avast security products in at least eight countries.

A critical security flaw has been uncovered in UNISOC's smartphone chipset that could be potentially weaponized to disrupt a smartphone's radio communications through a malformed packet. "Left unpatched, a hacker or a military unit can leverage such a vulnerability to neutralize communications in a specific location," Israeli cybersecurity company Check Point said in a report shared with The Hacker News.

The ten most prolific Android mobile banking trojans target 639 financial applications that collectively have over one billion downloads on the Google Play Store. Mobile banking trojans hide behind seemingly benign apps like productivity tools and games and commonly sneak into the Google Play Store, Android's official app store.
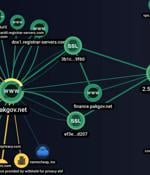
The threat actor known as SideWinder has added a new custom tool to its arsenal of malware that's being used in phishing attacks against Pakistani public and private sector entities. The custom tool identified by Group-IB, dubbed SideWinder.