Security News > 2024

A threat actor announced on a cybercrime forum that they sold the source code and a cracked version of the Zeppelin ransomware builder for just $500. The post was spotted by threat intelligence company KELA and while the legitimacy of the offer has not been validated, the screenshots from the seller indicate that the package is real. The seller of the Zeppelin source code and builder uses the handle 'RET' and clarified that they did not author the malware but simply managed to crack a builder version for it.

The U.S. Federal Trade Commission has started accepting submissions for its Voice Cloning Challenge, a public competition with a $25,000 top prize for ideas that protect consumers from the danger of AI-enabled voice cloning for fraudulent activity. AI can be used to clone someone's voice by analyzing an audio clip of the target speaking to extract unique vocal characteristics and then using the training data to generate new speech.

A weak password exposed by infostealer malware is being blamed after a massive outage at Orange Spain disrupted around half of its network's traffic. The malware had infected the account of an Orange Spain employee.

Section four of the "Executive Order on Improving the Nation’s Cybersecurity" introduced a lot of people in tech to the concept of a “Software Supply Chain” and securing it. If you make software...

Kaspersky researchers are detailing "An attack that over four years backdoored dozens if not thousands of iPhones, many of which belonged to employees of Moscow-based security firm Kaspersky." It's a zero-click exploit that makes use of four iPhone zero-days. It uses return/jump oriented programming and multiple stages written in the NSExpression/NSPredicate query language, patching the JavaScriptCore library environment to execute a privilege escalation exploit written in JavaScript.

Comment In some ways, the ransomware landscape in 2023 remained unchanged from the way it looked in previous years. The industry needs governments to insert themselves into the crisis and take decisive action to stop ransomware from becoming even more out of hand than it already is.
Three new malicious packages have been discovered in the Python Package Index (PyPI) open-source repository with capabilities to deploy a cryptocurrency miner on affected Linux devices. The three...

Four Chinese balloons have reportedly floated over the Taiwan Strait, three of them crossing over the island's land mass and near its Ching-Chuan-Kang air base before disappearing, according to the Taiwan's defense ministry. An appearance of a similar Chinese balloon caused quite a stir in the US last February.

Since these 3,000+ packages manage to include every single npm package on the npmjs.com registry as their dependency, npm package authors who have ever published to the npm registry would now be unable to remove their packages at will, because of npm's policy. Everything prevents you from unpublishing your packages.
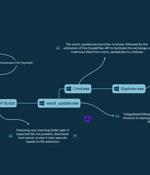
The threat actor known as UAC-0050 is leveraging phishing attacks to distribute Remcos RAT using new strategies to evade detection from security software. "The group's weapon of choice is Remcos...