Security News > 2024 > August

ThreatLocker has created a list of the top 15 actions to secure an organization if employing a remote or hybrid workforce. Learn more in this free e-book from ThreatLocker. [...]

The Seattle-Tacoma International Airport has confirmed that a cyberattack is likely behind the ongoing IT systems outage that disrupted reservation check-in systems and delayed flights over the...

Unprotected database with 12 years of biz records yanked offline Exclusive Nearly 2.7 TB of sensitive data — 31.5 million invoices, contracts, HIPPA patient consent forms, and other business...

This is a big deal. A US Appeals Court ruled that geofence warrants—these are general warrants demanding information about all people within a geographical boundary—are unconstitutional. The...

While CyberGhost VPN’s optimized servers bring a lot of value, NordVPN’s more consistent speed performance and extensive feature inclusions give it the slight edge.

Sueball suggests outsourcer went out of bounds by developing competing product A subsidiary of IT outsourcer Cognizant filed a lawsuit on Friday in Texas federal court alleging that rival Infosys...
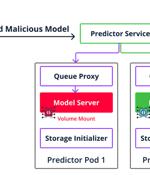
Cybersecurity researchers are warning about the security risks in the machine learning (ML) software supply chain following the discovery of more than 20 vulnerabilities that could be exploited to...

Nowadays, sensitive and critical data is traveling in everyday business channels that offer only the basic level of security and encryption, and companies are often oblivious to the risk. A case...

Two security vulnerabilities have been disclosed in the open-source Traccar GPS tracking system that could be potentially exploited by unauthenticated attackers to achieve remote code execution...

Cybersecurity researchers have uncovered new Android malware that can relay victims' contactless payment data from physical credit and debit cards to an attacker-controlled device with the goal of...