Security News > 2024 > June

CrowdStrike and Trellix are two of the top EDR software options on the market. CrowdStrike is a cloud-based EDR tool that protects endpoints from critical vulnerabilities such as malware, phishing, and ransomware and DDoS attacks.

Microsoft is warning about the potential abuse of Azure Service Tags by malicious actors to forge requests from a trusted service and get around firewall rules, thereby allowing them to gain...

About Bruce Schneier I am a public-interest technologist, working at the intersection of security, technology, and people. I've been writing about security issues on my blog since 2004, and in my monthly newsletter since 1998.

Google has revealed that it took down 1,320 YouTube channels and 1,177 Blogger blogs as part of a coordinated influence operation connected to the People’s Republic of China (PRC). "The...

This is why a network security policy must be in place to create security guidelines for devices that transport and store company data. To protect company data and reputation, it is essential to ensure the network is secured from unauthorized access, data loss, malware infestations and security breaches.
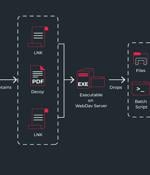
Cybersecurity researchers have disclosed details of a threat actor known as Sticky Werewolf that has been linked to cyber attacks targeting entities in Russia and Belarus. The phishing attacks...

As we integrate AI more deeply into vulnerability management processes, organizations can expect enhanced security postures and a shift towards a more proactive and predictive approach to handling cybersecurity threats. AI has some major limitations and even security concerns, especially regarding vulnerability management.

Radare is an open-source UNIX-like reverse engineering framework and command-line toolset. "I started the project in 2006 when I was working as a forensic analyst, and I wrote a simple command-line hexadecimal editor to scan a hard drive looking for keywords and dump the results to disk to recover some files. Over time, the project evolved to meet my diverse requirements, serving as a debugger, a disassembler, and a platform for exploring various architectures. It proved invaluable during CTF competitions, at work, and for personal reverse engineering projects," Sergi Àlvarez, the creator of Radare, told Help Net Security.

CISOs who elevate response and recovery to equal status with prevention are generating more value than those who adhere to outdated zero tolerance for failure mindsets, according to Gartner. "Each new cybersecurity disruption exposes the fact that CISOs manage more through adrenaline than intention, which is unsustainable," said Dennis Xu, VP Analyst at Gartner.

75% of security professionals had to change their cybersecurity strategy in the last year due to the rise in AI-powered cyber threats, with 73% expressing a greater focus on prevention capabilities, according to Deep Instinct. 97% of respondents are concerned their organization will suffer a security incident due to adversarial AI. "The biggest challenge for SecOps teams is keeping pace with the rapidly evolving threat landscape being driven by AI. These never-before-seen threats are disrupting organizations, causing breaches that are accompanied by costly remediation. SecOps must stay ahead of these unknown attacks that often penetrate existing defenses, despite investment in technology and talented cybersecurity professionals," said Lane Bess, CEO of Deep Instinct.