Security News > 2024 > May

Rockwell Automation warned customers to disconnect all industrial control systems not designed for online exposure from the Internet due to increasing malicious activity worldwide.Network defenders should never configure such devices to allow remote connections from systems outside the local network.

Your profile can be used to present content that appears more relevant based on your possible interests, such as by adapting the order in which content is shown to you, so that it is even easier for you to find content that matches your interests. Content presented to you on this service can be based on your content personalisation profiles, which can reflect your activity on this or other services, possible interests and personal aspects.

GitHub has rolled out fixes to address a maximum severity flaw in the GitHub Enterprise Server (GHES) that could allow an attacker to bypass authentication protections. Tracked...

GitHub has fixed a maximum severity (CVSS v4 score: 10.0) authentication bypass vulnerability tracked as CVE-2024-4986, which impacts GitHub Enterprise Server (GHES) instances using SAML single...

Google is rolling out a server-side fix for a known issue affecting the Chrome browser that causes webpage content to temporarily disappear when users change between open tabs. "We are aware of an issue impacting Chrome Browser that may result in webpage content temporarily disappearing when switching between open tabs," a Google Chrome Support Manager said in a post on the company's community website.

A new attack campaign dubbed CLOUD#REVERSER has been observed leveraging legitimate cloud storage services like Google Drive and Dropbox to stage malicious payloads. "The VBScript and PowerShell...

Researchers have found 15 vulnerabilities in QNAP's network attached storage devices, and have released a proof-of-concept for one: an unauthenticated stack overflow vulnerability that may be leveraged for remote code execution. "Given the shared-access model of the NAS device, which permits sharing files with specific users, both authenticated and unauthenticated bugs were of interest to us," they said.
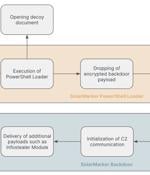
The persistent threat actors behind the SolarMarker information-stealing malware have established a multi-tiered infrastructure to complicate law enforcement takedown efforts, new findings from...

Zoom has announced the global availability of post-quantum end-to-end encryption for Zoom Meetings, with Zoom Phone and Zoom Rooms to follow soon. Meetings is a popular video conferencing service that allows users to host and join virtual meetings with high-definition video and audio, featuring screen sharing, chat, and participant management, making it a popular choice for businesses, virtual events, and online classes.
One of the enduring challenges of building modern applications is to make them more secure without disrupting high-velocity DevOps processes or degrading the developer experience. Today’s cyber...