Security News > 2024 > April

On March 27 the commission asked telecommunications providers to weigh in and detail what they are doing to prevent SS7 and Diameter vulnerabilities from being misused to track consumers' locations. The FCC has also asked carriers to detail any exploits of the protocols since 2018.
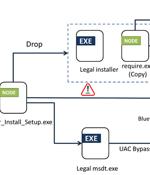
Bogus installers for Adobe Acrobat Reader are being used to distribute a new multi-functional malware dubbed Byakugan. The starting point of the attack is a PDF file written in Portuguese that,...

Financial organizations in the Asia-Pacific (APAC) and Middle East and North Africa (MENA) are being targeted by a new version of an "evolving threat" called JSOutProx. "JSOutProx is a...

Multiple China-nexus threat actors have been linked to the zero-day exploitation of three security flaws impacting Ivanti appliances (CVE-2023-46805, CVE-2024-21887, and CVE-2024-21893). The...

Your profile can be used to present content that appears more relevant based on your possible interests, such as by adapting the order in which content is shown to you, so that it is even easier for you to find content that matches your interests. Content presented to you on this service can be based on your content personalisation profiles, which can reflect your activity on this or other services, possible interests and personal aspects.

Browser fingerprinting is one of many tactics phishing site authors use to evade security checks and lengthen the lifespan of malicious campaigns. While browser fingerprinting has been used by legitimate organizations to uniquely identify web browsers for nearly 15 years, it is now also commonly exploited by cybercriminals: a recent study shows one in four phishing sites using some form of this technique.

The study also found that AI integration into cybersecurity is not just a concept but also a practical reality for many, with 67% of respondents stating that they have tested AI specifically for security purposes. As for the ability to leverage AI, 48% of professionals expressed confidence in their organization's ability to execute a strategy for leveraging AI in security, with 28% feeling reasonably confident and 20% very confident.

"Since the pandemic, employees have gained unprecedented flexibility in where and how they work, and that flexibility often extends to the apps and devices they use. Productivity has become paramount, leaving significant security challenges for IT and security leaders-who often feel like they don't have bandwidth or budget to keep employees secure," said Jeff Shiner, CEO of 1Password. 69% admit they're at least partly reactive when it comes to security.

As businesses evolve, they often experience changes in roles, partnerships, and staff turnover. This dynamic can result in improper access to data and resources.

Your profile can be used to present content that appears more relevant based on your possible interests, such as by adapting the order in which content is shown to you, so that it is even easier for you to find content that matches your interests. Content presented to you on this service can be based on your content personalisation profiles, which can reflect your activity on this or other services, possible interests and personal aspects.