Security News > 2024 > February

Group-IB identified a large-scale malicious campaign primarily targeting job search and retail websites of companies in the Asia-Pacific region. ResumeLooters is confirmed to have stolen several databases containing 2,079,027 unique emails and other records, such as names, phone numbers, dates of birth, and information about job seekers' experience and employment history.

At least 25 new ransomware gangs emerged in 2023, with Akira and 8Base proving the most "Successful," research reveals. The gangs were the two "Success" stories of the year for cybercrooks, proving that the lure of big ransom payouts is still enough to attract significant interest from fledgling ransomware operations, despite the challenges that remain for newcomers.
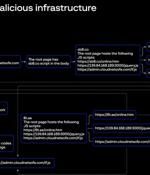
Employment agencies and retail companies chiefly located in the Asia-Pacific (APAC) region have been targeted by a previously undocumented threat actor known as ResumeLooters since early 2023 with...

TL;DR: Learn how to stop cyber criminals with the Cyber Security Specialist Workshop, featuring 16 live training sessions, now just $499.99 for a limited time. Want a career that offers longevity as well as a great salary to boot? Then start preparing now for the opportunities that come with the Cyber Security Specialist Workshop, offered at half price for a limited time.

Five days after Mastodon developers pushed out fixes for a remotely exploitable account takeover vulnerability, over 66% of Mastodon servers out there have been upgraded to close the hole. Mastodon is open-source software for running self-hosted social networking services within the wider Fediverse.

A threat group named 'ResumeLooters' has stolen the personal data of over two million job seekers after compromising 65 legitimate job listing and retail sites using SQL injection and cross-site scripting attacks. ResumeLooters primarily employs SQL injection and XSS to breach targeted sites, mainly job-seeking and retail shops.

A recently disclosed server-side request forgery (SSRF) vulnerability impacting Ivanti Connect Secure and Policy Secure products has come under mass exploitation. The Shadowserver...

How do security validations contribute to an organization's understanding of its security posture and risk profile? Third party security validation is a helpful tool, but typically is only part of the analysis required to understand the entire posture and effectiveness of a security program.

In today's increasingly automated operational environment, crypto agility-i.e., an organization's ability to switch rapidly and seamlessly between certificate authorities, encryption standards and keys and certificates with minimal disruption to one's digital infrastructure-becomes essential to business. In 2020, Apple reduced the lifespan certificates to a year, pushing others to match them, and in March 2023, Google announced a proposal to reduce TLS certificate validity to 90 days.

Our list of cybersecurity books has been curated to steer your professional growth in 2024. The book is packed with mental models, notes, and advice to help early-stage cybersecurity founders get their ideas off the ground and solve problems young companies face around problem discovery, hiring, building products, and fundraising.