Security News > 2023 > July
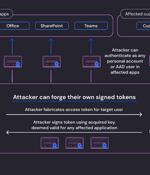
According to cloud security company Wiz, the inactive Microsoft account consumer signing key used to forge Azure Active Directory tokens to gain illicit access to Outlook Web Access and Outlook.com could also have allowed the adversary to forge access tokens for various types of Azure AD applications. Wiz's analysis fills in some of the blanks, with the company discovering that "All Azure personal account v2.0 applications depend on a list of 8 public keys, and all Azure multi-tenant v2.0 applications with Microsoft account enabled depend on a list of 7 public keys."
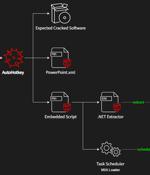
A new variant of AsyncRAT malware dubbed HotRat is being distributed via free, pirated versions of popular software and utilities such as video games, image and sound editing software, and Microsoft Office. "HotRat malware equips attackers with a wide array of capabilities, such as stealing login credentials, cryptocurrency wallets, screen capturing, keylogging, installing more malware, and gaining access to or altering clipboard data," Avast security researcher Martin a Milánek said.

The US government is warning that threat actors breached the network of a U.S. organization in the critical infrastructure sector after exploiting a zero-day RCE vulnerability currently identified as CVE-2023-3519, a critical-severity issue in NetScaler ADC and Gateway that Citrix patched this week. Because the targeted NetScaler ADC appliance was in a segregated environment on the network, the hackers were not able to move laterally to a domain controller, CISA says.

Threat actors have breached the network of a U.S. organization in the critical infrastructure sector after exploiting a zero-day RCE vulnerability currently identified as CVE-2023-3519, a critical-severity issue in NetScaler ADC and Gateway that Citrix patched this week.Because the targeted NetScaler ADC appliance was in a segregated environment on the network, the hackers were not able to move laterally to a domain controller, CISA says.

North Korean state-sponsored hackers have been linked to two recent cyberattack campaigns: one involving a spear-phishing attack on JumpCloud and the other targeting tech employees on GitHub through a social engineering campaign. "Fewer than 5 JumpCloud customers were impacted and fewer than 10 devices total were impacted, out of more than 200,000 organizations who rely on the JumpCloud platform for a variety of identity, access, security, and management functions,".

"BundleBot is abusing the dotnet bundle, self-contained format that results in very low or no static detection at all," Check Point said in a report published this week, adding it is "Commonly distributed via Facebook Ads and compromised accounts leading to websites masquerading as regular program utilities, AI tools, and games." NET single-file, self-contained application that, in turn, incorporates a DLL file, whose responsibility is to fetch a password-protected ZIP archive from Google Drive.

The U.S. Justice Department and the Federal Trade Commission announced that Amazon has agreed to pay a $25 million fine to settle alleged children's privacy laws violations related to the company's Alexa voice assistant service. Amazon also faces a $5 million fine for privacy violations associated with its Ring video doorbell service.

As most local governments maintain a small IT staff, there is potential for shared passwords, reused credentials, and a lack of multi-factor authentication security, exposing vulnerabilities for a breach. The Play ransomware group claimed responsibility for breaching city services and posted about the hack on their group website.

AI is about to make this issue much more complicated, and could drastically expand the types of laws that can be enforced in this manner. Some legal scholars predict that computationally personalized law and its automated enforcement are the future of law.

The exploitation of the Citrix NetScaler ADC zero-day vulnerability was first spotted by a critical infrastructure organization, who reported it to the Cybersecurity and Infrastructure Security Agency. "In June 2023, threat actors exploited this vulnerability as a zero-day to drop a webshell on a critical infrastructure organization's non-production environment NetScaler ADC appliance. The webshell enabled the actors to perform discovery on the victim's active directory and collect and exfiltrate AD data. The actors attempted to move laterally to a domain controller but network-segmentation controls for the appliance blocked movement," the agency shared in an advisory published on Thursday.