Security News > 2023 > June

Google Workspace has a weak spot that can prevent the discovery of data exfiltration from Google Drive by a malicious outsider or insider, Mitiga researchers say. "Google Workspace provides visibility into a company's Google Drive resources using 'Drive log events,' for actions such as copying, deleting, downloading, and viewing files. Events that involve external domains also get recorded, like sharing an object with an external user," Mitiga's Ariel Szarf and Or Aspir explained.

Researchers have discovered a novel attack on the Python Package Index repository that employs compiled Python code to sidestep detection by application security tools. PYC files are compiled bytecode files that are generated by the Python interpreter when a Python program is executed.

Threat actors can exploit the lack of appropriate security controls, like poor configuration management, to compromise an organization's security. IT hygiene is critical for maintaining the security and resilience of an organization's IT infrastructure.

Mitigating the risk of extinction from AI should be a global priority alongside other societal-scale risks such as pandemics and nuclear war. I actually don't think that AI poses a risk to human extinction.
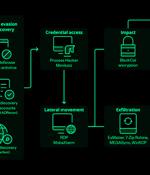
The threat actors behind BlackCat ransomware have come up with an improved variant that prioritizes speed and stealth in an attempt to bypass security guardrails and achieve their goals. Active since November 2021, it has emerged as a formidable ransomware actor, victimizing more than 350 targets as of May 2023.

CVE-2023-28771, the critical command injection vulnerability affecting many Zyxel firewalls, is being actively exploited by a Mirai-like botnet, and has been added to CISA's Known Exploited Vulnerabilities catalog. CVE-2023-28771 is a vulnerability that allows unauthenticated attackers to execute OS commands remotely by sending crafted IKE packets to an affected device.

Cybersecurity researchers have offered a closer look at the RokRAT remote access trojan that's employed by the North Korean state-sponsored actor known as ScarCruft. "RokRAT is a sophisticated remote access trojan that has been observed as a critical component within the attack chain, enabling the threat actors to gain unauthorized access, exfiltrate sensitive information, and potentially maintain persistent control over compromised systems," ThreatMon said.

The e-tail giant's Ring home security cam subsidiary was accused of "Compromising its customers' privacy by allowing any employee or contractor to access consumers' private videos and by failing to implement basic privacy and security protections, enabling hackers to take control of consumers' accounts, cameras, and videos." The FTC complaint also alleges Ring knew its cloud services were susceptible to credential stuffing and brute-force attacks but did little to stymie such efforts.

A change in the deployment of the RomCom malware strain has illustrated the blurring distinction between cyberattacks motivated by money and those fueled by geopolitics, in this case Russia's illegal invasion of Ukraine, according to Trend Micro analysts. The infosec vendor pointed out that RomCom's operators, threat group Void Rabisu, also has links to the notorious Cuba ransomware, and therefore assessed it was assumed to be a financially driven criminal organization.

As cloud adoption pervades, one of the bigger security and privacy challenges for cloud service customers is having to relinquish a significant amount of control and ownership of their data and infrastructure to cloud service providers. Every CSP will implement security differently and every cloud model will have varying degrees of security control ownership, which is why it might be difficult for them to meet all security requirements.