Security News > 2023 > April

The Mirai malware botnet is actively exploiting a TP-Link Archer A21 WiFi router vulnerability tracked as CVE-2023-1389 to incorporate devices into DDoS swarms. Researchers first abused the flaw during the Pwn2Own Toronto hacking event in December 2022, where two separate hacking teams breached the device using different pathways.
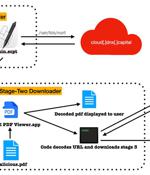
A financially-motivated North Korean threat actor is suspected to be behind a new Apple macOS malware strain called RustBucket. The Apple device management company attributed it to a threat actor known as BlueNoroff, a subgroup within the infamous Lazarus cluster that's also tracked under the monikers APT28, Nickel Gladstone, Sapphire Sleet, Stardust Chollima, and TA444.

Google has made available a new tool for Google Workspace admins and security teams to make an assessment of the risk different Chrome extensions may present to their users: Spin.AI App Risk Assessment. The tool is available through the Chrome Browser Cloud Management console and provides admins with valuable insights into potential security threats.

Google's cloud division is following in the footsteps of Microsoft with the launch of Security AI Workbench that leverages generative AI models to gain better visibility into the threat landscape.Users, like with Microsoft's GPT-4-based Security Copilot, can "Conversationally search, analyze, and investigate security data" with an aim to reduce mean time-to-respond as well as quickly determine the full scope of events.

Following a report on its activities, the Israeli spyware company QuaDream has shut down. Based on an analysis of samples shared with us by Microsoft Threat Intelligence, we developed indicators that enabled us to identify at least five civil society victims of QuaDream's spyware and exploits in North America, Central Asia, Southeast Asia, Europe, and the Middle East.

In half of investigations included in the report, attackers exploited ProxyShell and Log4Shell vulnerabilities-vulnerabilities from 2021-to infiltrate organizations. "When today's attackers aren't breaking in, they're logging in. The reality is that the threat environment has grown in volume and complexity to the point where there are no discernible gaps for defenders to exploit. For most organizations, the days of going at it alone are well behind them. It truly is everything, everywhere, all at once. However, there are tools and services available to businesses that can alleviate some of the defensive burden, allowing them to focus on their core business priorities," said John Shier, field CTO, commercial, Sophos.

An unauthenticated RCE flaw in widely-used PaperCut MF and NG print management software is being exploited by attackers to take over vulnerable application servers, and now there's a public PoC exploit. According to PaperCut, the attacks seem to have started on April 14, 2023 - a month and a week after the software maker released new PaperCut MF and NG versions that fixed CVE-2023-27350 and CVE-2023-27351, an unauthenticated information disclosure flaw that could allow attackers to access sensitive user information without authentication.

The report found that a majority of modern phishing attacks rely on stolen credentials and outlined the growing threat from Adversary-in-the-Middle attacks, increased use of the InterPlanetary File System, as well as reliance on phishing kits sourced from black markets and AI tools like ChatGPT. "Phishing remains one of the most prevalent threat vectors cybercriminals utilize to breach global organizations. Year-over-year, we continue to see an increase in the number of phishing attacks which are becoming more sophisticated in nature. Threat actors are leveraging phishing kits & AI tools to launch highly effective e-mail, SMiShing, and Vishing campaigns at scale"," said Deepen Desai, Global CISO and Head of Security, Zscaler. "AitM attacks supported by growth in Phishing-as-a-Service have allowed attackers to bypass traditional security models, including multi-factor authentication. To protect their environment, organizations should adopt a zero trust architecture to significantly minimize the attack surface, prevent compromise, and reduce the blast radius in case of a successful attack," added Desai.
"This change means users are better protected from lockout and that services can rely on users retaining access, increasing both convenience and security," Google's Christiaan Brand said. The update, which also brings a new icon to the two-factor authenticator app, finally brings it in line with Apple's iCloud Keychain and addresses a long-standing complaint that it's tied to the device on which it's installed, making it a hassle when switching between phones.

As digital transformation revolutionizes the healthcare industry, its use of API technology is skyrocketing. APIs, which help users and apps interact and exchange information, are essential tools for healthcare systems striving to achieve greater interoperability.