Security News > 2023 > March
A pair of severe security vulnerabilities have been disclosed in the Jenkins open source automation server that could lead to code execution on targeted systems. The flaws, tracked as CVE-2023-27898 and CVE-2023-27905, impact the Jenkins server and Update Center, and have been collectively christened CorePlague by cloud security firm Aqua.
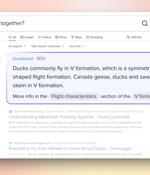
Privacy-focused search engine DuckDuckGo has launched the first beta version of DuckAssist, an AI-assisted feature that writes accurate summaries to answer users' search queries. DuckAssist uses OpenAI's natural language technology to generate answers to user's search queries at the top of the search results page, making responses more direct than traditional search results.

It's common for organizations to feel compelled to cut costs by exchanging their pen testers for scanners. Traditionally, most businesses have tested their network and application security through pen testing; pen testing can theoretically be performed by red teams internal to an organization but is typically outsourced to contractors in practice.

This can leave gaps in an enterprise's ability to identify devices that are accessing the network and in ensuring that those devices are compliant with security policies. As part of the market's need to gain a clearer, real-time picture of their devices and security posture, Syxsense launched its Enterprise platform last year to address the three key elements of endpoint management and security: vulnerabilities, patch, and compliance.

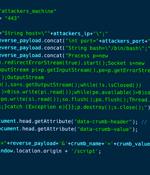
Researchers have discovered malware that "Can hijack a computer's boot process even when Secure Boot and other advanced protections are enabled and running on fully updated versions of Windows." Dubbed BlackLotus, the malware is what's known as a UEFI bootkit.

TechRepublic Premium Risk management policy SUMMARY Risk management involves the practice of addressing and handling threats to the organization in the form of cybersecurity attacks and compromised or lost data. The process of establishing appropriate risk management guidelines is critical to ensure company operations and reputation do not suffer adverse impacts.

TechRepublic Premium Offshore work policy It's common practice for companies to use offshore employees or contractors in order to offload work to specialized individuals or reduce costs associated with certain tasks and responsibilities. This can free up staff to focus on more complex and valuable initiatives, and also ensure 24×7 operations for companies which rely upon on-call staff and subject-matter .....

The North Korea-linked Lazarus Group has been observed weaponizing flaws in an undisclosed software to breach a financial business entity in South Korea twice within a span of a year. While the first attack in May 2022 entailed the use of a vulnerable version of a certificate software that's widely used by public institutions and universities, the re-infiltration in October 2022 involved the exploitation of a zero-day in the same program.

Passwords are also regularly shared between coworkers, but password management solutions can significantly mitigate the risks involved in colleagues using the same password to share access or data. Reuse of passwords - using the same password for more than one account - can result in a multiplicity of problems should that password become compromised.

High-profile government entities in Southeast Asia are the target of a cyber espionage campaign undertaken by a Chinese threat actor known as Sharp Panda since late last year. The intrusions are characterized by the use of a new version of the Soul modular framework, marking a departure from the group's attack chains observed in 2021.