Security News > 2023 > February

Many online stores are exposing private backups in public folders, including internal account passwords, which can be leveraged to take over the e-commerce sites and extort owners. According to a study by website security company Sansec, roughly 12% of online stores forget their backups in public folders due to human error or negligence.

A new version of the Medusa DDoS botnet, based on Mirai code, has appeared in the wild, featuring a ransomware module and a Telnet brute-forcer. Medusa is an old malware strain being advertised in darknet markets since 2015, which later added HTTP-based DDoS capabilities in 2017.

A joint law enforcement operation conducted by Germany, the Netherlands, and Poland has cracked yet another encrypted messaging application named Exclu used by organized crime groups. "Exclu makes it possible to exchange messages, photos, notes, voice memos, chat conversations, and videos with other users," the Politie said.

CVE-2021-21974 is a vulnerability affecting OpenSLP as used in VMware ESXi. The French government's Computer Emergency Response Team CERT-FR was the first to raise an alert on ransomware exploiting this vulnerability on Feb. 3, 2023, quickly followed by French hosting provider OVH. Attackers can exploit the vulnerability remotely and unauthenticated via port 427, which is a protocol that most VMware customers do not use.

Toyota's Global Supplier Preparation Information Management System was breached by a security researcher who responsibly reported the issue to the company. The issues were responsibly disclosed to Toyota on November 3, 2022, and the Japanese car maker confirmed they had been fixed by November 23, 2022.

Too many online store administrators are storing private backups in public folders and exposing database passwords, secret API keys, administrator URLs and customer data to attackers who know where to look. The researchers have analyzed 2037 online stores of various sizes and running of various e-commerce platforms and found that 250 of them stored archive files in the public web folder, accessible to all.
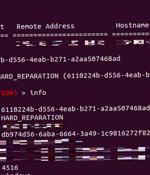
Threat actors are leveraging known flaws in Sunlogin software to deploy the Sliver command-and-control framework for carrying out post-exploitation activities. The findings come from AhnLab Security Emergency response Center, which found that security vulnerabilities in Sunlogin, a remote desktop program developed in China, are being abused to deploy a wide range of payloads.

Among these are a mandate to enforce multi-factor authentication across all admin access in a network environment as well as protect all privileged accounts, specifically machine-to-machine connections known as service accounts. How do you compile an accurate list of every admin user? While some can be easily identified - for example, IT and helpdesk staff - what about so-called shadow admins? These include former employees that may have left without deleting their admin accounts, which then continue to exist in the environment along with their privileged access.

Flawed encryption logic used in Cl0p ransomware's Linux variant has allowed SentinelOne researchers to create and release a free decryptor. "The [Cl0p] Windows variant encrypts the generated RC4 key responsible for the file encryption using the asymmetric algorithm RSA and a public key. In the Linux variant, the generated RC4 key is encrypted with a RC4 [hardcoded] 'master-key'," the researchers explained.

Criminals using Google search ads to deliver malware isn't new, but Ars Technica declared that the problem has become much worse recently. In the past, these families typically relied on phishing and malicious spam that attached Microsoft Word documents with booby-trapped macros.