Security News > 2022 > December
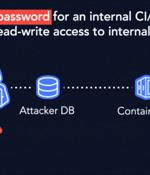
IBM has fixed a high-severity security vulnerability affecting its Cloud Databases for PostgreSQL product that could be potentially exploited to tamper with internal repositories and run unauthorized code. The privilege escalation flaw, dubbed "Hell's Keychain" by cloud security firm Wiz, has been described as a "First-of-its-kind supply-chain attack vector impacting a cloud provider's infrastructure."

A previously undocumented Go-based malware is targeting Redis servers with the goal of taking control of the infected systems and likely building a botnet network. The attacks involve taking advantage of a critical security vulnerability in the open source, in-memory, key-value store that was disclosed earlier this year to deploy Redigo, according to cloud security firm Aqua.

A previously undocumented Go-based malware is targeting Redis servers with the goal of taking control of the infected systems and likely building a botnet network. The attacks involve taking advantage of a critical security vulnerability in the open source, in-memory, key-value store that was disclosed earlier this year to deploy Redigo, according to cloud security firm Aqua.

A sophisticated and very patient threat group behind a global malvertising scheme is using so-called aged domains to skirt past cybersecurity tools and catch victims in investment scams. Cybercriminals who run malvertising campaigns typically will spin up a domain and quickly put it into use.

The new Cyber Incident Reporting for Critical Infrastructure Act of 2022 requires CISA to create rules regarding cyber incident reporting by critical infrastructure organizations. CISA will share data from cyber incident reports, including defensive measures and anonymized cyber threat indicators, with other organizations.

The new Cyber Incident Reporting for Critical Infrastructure Act of 2022 requires CISA to create rules regarding cyber incident reporting by critical infrastructure organizations. CISA will share data from cyber incident reports, including defensive measures and anonymized cyber threat indicators, with other organizations.

After a lengthy discussion between staff at Mozilla and Apple, security researchers and the CA itself, Mozilla program manager Kathleen Wilson said the org's concerns were "Substantiated" enough to set a distrust date of November 30 for TrustCor's root certificates. Microsoft didn't participate in the conversation; instead, TrustCor executive Rachel McPherson claimed that Microsoft had set a distrust date of November 1 for her company's certs.

Multiple unpatched vulnerabilities have been discovered in three Android apps that allow a smartphone to be used as a remote keyboard and mouse. The apps in question are Lazy Mouse, PC Keyboard, and Telepad, which have been cumulatively downloaded over two million times from the Google Play Store.

Multiple unpatched vulnerabilities have been discovered in three Android apps that allow a smartphone to be used as a remote keyboard and mouse. The apps in question are Lazy Mouse, PC Keyboard, and Telepad, which have been cumulatively downloaded over two million times from the Google Play Store.

Bob proudly described to The Register that those racks were properly resilient: a pair of firewalls and two sets of switches connected to primary and secondary circuits. "One day, we got a call from the managed network provider," Bob told On-Call.