Security News > 2022 > December

"The end objective of this campaign appears to be to gain access to mobile carrier networks and, as evidenced in two investigations, perform SIM swapping activity," CrowdStrike researcher Tim Parisi said in an analysis published last week. Initial access to the target environment is said to be undertaken through a variety of methods ranging from social engineering using phone calls and messages sent via Telegram to impersonate IT personnel.

Review and manage your consent Here's an overview of our use of cookies, similar technologies and how to manage them. You wonder which mountain to scale first, but it is an impossible choice.
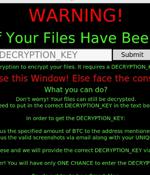
A version of an open source ransomware toolkit called Cryptonite has been observed in the wild with wiper capabilities due to its "Weak architecture and programming." Written in Python, the malware employs the Fernet module of the cryptography package to encrypt files with a ".

If you want to get cloud migration right, you must deal with an inconvenient truth: Cloud or hybrid cloud environments lower the drawbridge between your data center and the internet, and that creates opportunity as well as security risk. Cloud migration cannot succeed without reevaluating the role of DDI services in your enterprise.

With so many manufacturers and devices to choose from, the smart home landscape is often a mishmash of support and usability. Simply put, until now, the lack of a unifying standard among various smart home technology standards made using devices together complicated and difficult.

In this Help Net Security video, Roman Faithfull, Cyber Intelligence Analyst at Digital Shadows, talks about how threat actors mobilize new members within the cybercriminal ecosystem. Cybercriminal forums are awash with users advertising and requesting the services of developers to design fresh new malware.

Norton released its top cyber trends to watch in 2023, emphasizing that the economy will have the greatest impact on the spread of cybercrime next year. Experts predict the pressures associated with economic uncertainty and rising costs will create the perfect environment for scammers to take advantage of people when they are more vulnerable.

The transformation comes as 68% of respondents cite their fears about API sprawl. Ensuring data security and controlling API sprawl were top concerns, with 68% worrying about complexity due to sprawl and 48% of respondents ranking "Increased security challenges" as their single greatest concern with API growth.

America's Transport Security Administration, better known as the TSA, has been testing facial recognition software to automatically screen passengers flying across the country in 16 airports. The equipment will snap a live photo of their face and check whether it matches with the one captured on their ID. The pilot program, testing the Credential Authentication Technology 2 system, aims to reduce security screening wait times by automating the process so TSA agents do not need to manually check IDs.

Four men suspected of plotting to commit wire fraud and identity theft have been arrested and now face extradition to America. It is alleged they conspired to break into US companies' servers, steal people's personally identifiable information, use that info to file fraudulent tax returns to Uncle Sam, and collect victims' tax refunds.