Security News > 2022 > October

The number of cyberattacks directed at artificial intelligence continues to increase, and hackers are no longer planting malicious bugs within code - their techniques have become increasingly complex, allowing them to tamper with systems to compromise and "Weaponize" AI against the organizations leveraging it for their operations. There are four typical elements to consider when it comes to ML. The first is data sets: the data provided to a device or machine so it can function, review, and decide based on the information received.

Australian health insurance firm Medibank on Wednesday disclosed that the personal information of all of its customers had been unauthorizedly accessed following a recent ransomware attack.In an update to its ongoing investigation into the incident, the firm said the attackers had access to "Significant amounts of health claims data" as well as personal data belonging to its ahm health insurance subsidiary and international students.
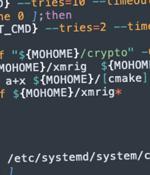
A new cryptojacking campaign has been uncovered targeting vulnerable Docker and Kubernetes infrastructures as part of opportunistic attacks designed to illicitly mine cryptocurrency. Cybersecurity company CrowdStrike dubbed the activity Kiss-a-dog, with its command-and-control infrastructure overlapping with those associated with other groups like TeamTNT, which are known to strike misconfigured Docker and Kubernetes instances.

A stealthy cryptocurrency mining operation has been spotted using thousands of free accounts on GitHub, Heroku and other DevOps outfits to craft digital tokens. Sysdig estimated each of those 30 free GitHub accounts cost the Microsoft-owned giant $15 per month, and the free tier accounts from Heroku, Buddy and others cost providers between $7 and $10 per month.

In this interview for Help Net Security, Camellia Chan, CEO at Flexxon, talks about the dangers of closed-circuit television (CCTV) hacks and what users can do to protect themselves. More and more...

In this Help Net Security video, Christopher Maddalena, Director of Internal and Community Product at SpecterOps, showcases Ghostwriter, which helps you manage clients, projects, reports, and infrastructure in one application. The tool does not replace some of the more common or traditional project management tools, such as CRMs. Still, it does consolidate all relevant project information in a way for users to easily curate every aspect of their projects.

Dark data is data that a company has collected but no longer needs - ranging from outdated customer information to old employee records. This data type is often forgotten and unprotected by corporations, creating substantial liabilities and tempting targets for cybercriminals.

Beginning in Autumn 2024, existing photo-less national health insurance cards will no longer be accepted, officially replaced by My Number Cards. There's only one problem: Japan residents seem reluctant to adopt them, with an online petition to keep current health cards quickly gathering 100,000 signatures.

Employer demand for cybersecurity professionals continues to strain talent availability, according to new data from CyberSeek. For the 12-month period ending in September 2022, employers listed 769,736 openings for cybersecurity positions or jobs requiring cybersecurity skills.

Check Point Research has published its Brand Phishing Report for Q3 2022, which highlights the brands which were most frequently imitated by criminals in their attempts to steal individuals’...