Security News > 2022 > April
Security from Device to SaaS - securing a SaaS environment isn't enough when it comes to protecting against a breach. SSO does not go far enough, and organizations that take SaaS security seriously must also include MFA security measures.

Other key findings Of the respondents that said their organization paid a cyber ransom to regain access to data, applications, and/or systems after an attack, only 14% were able to recover all of their data. 87% of respondents who made ransom payments said that they experienced additional extortion attempts beyond the initial ransomware demand.

While many developers acknowledge the importance of applying a security-led approach in the software development lifecycle, 86% do not view application security as a top priority when writing code. These are primarily due to time constraints to meet deadlines, or developers not having enough training or guidance on how to implement secure coding from their managers.

In this video for Help Net Security, Charles Brook, Threat Intelligence Researcher at Tessian, talks about how cybercriminals have taken advantage of the crisis in Ukraine to create charity donation scams. While there are legitimate ways to donate money and resources, scammers have started using impersonation techniques and sneaky tactics to dupe individuals into sending fake donations via emails, asking for cryptocurrency, or via fake websites.

The XM Cyber research team analyzed the methods, attack paths and impacts of attack techniques that imperil critical assets across on-prem, multi-cloud and hybrid environments. They fail to show how these seemingly unrelated issues form hidden attack paths that hackers can use to pivot through a hybrid cloud environment and compromise critical assets.
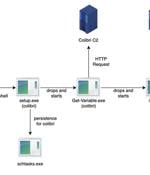
Cybersecurity researchers have detailed a "Simple but efficient" persistence mechanism adopted by a relatively nascent malware loader called Colibri, which has been observed deploying a Windows information stealer known as Vidar as part of a new campaign. "The attack starts with a malicious Word document deploying a Colibri bot that then delivers the Vidar Stealer," Malwarebytes Labs said in an analysis.

Puppet revealed the findings of its report which revealed how the post-pandemic environment directly impacted DevOps salaries as organizations invest in competitive compensation and top talent. "The gradual decrease in a wage gap hopefully points to a long-term shift in pay equity. As a DevOps leader, I am inspired by this progression and I look forward to seeing more equality in wages and gender parity across DevOps overall."

The embedded security market size is projected to grow from $6.8 billion in 2022 to $9 billion by 2027; it is expected to grow at a CAGR of 5.9% from 2022 to 2027, according to MarketsandMarkets. The key factors contributing to the growth of the embedded security market include increasing use of IoT-based applications, payments functionality in wearables, increasing cyber threats.

VMware has released security updates to patch eight vulnerabilities spanning its products, some of which could be exploited to launch remote code execution attacks. Credited with reporting all the vulnerabilities is Steven Seeley of Qihoo 360 Vulnerability Research Institute.

American cybersecurity company Palo Alto Networks warned customers on Wednesday that some of its firewall, VPN, and XDR products are vulnerable to a high severity OpenSSL infinite loop bug disclosed three weeks ago.Even though the OpenSSL team released a patch two weeks ago when it publicly disclosed the bug, customers will have to wait until later this month when Palo Alto Networks plans to release security updates.