Security News > 2022 > January

Microsoft's first Patch Tuesday of 2022 has, for some folk, broken Hyper-V and sent domain controllers into boot loops. As well as the broken Hyper-V, popular tech blog Born City noted problems with boot loops on domain controllers, with other versions of Windows Server affected.

Ukrainian police officers have arrested a ransomware affiliate group responsible for attacking at least 50 companies in the U.S. and Europe. A 36-year-old resident of Ukraine's capital Kiev was identified as the leader of the group, which included his wife and three other acquaintances, the police states.

The Dutch Initiative for Vulnerability Disclosure has scored $100k towards its founder's hope of a nationwide bug bounty available for anything at all. The DIVD's $100k cash injection is from infosec outfit Huntress Labs and is part of a grand vision aimed at discouraging individual researchers from dumping vulns online, the organisation's founder Victor Gevers told The Register.

For threat actors, there is a simple calculus at play - namely, what method of attack is a) easiest and b) most likely to yield the biggest return? And the answer, at this moment, is Linux-based cloud infrastructure, which makes up 80%+ of the total cloud infrastructure. These attacks will undoubtedly continue into 2022 and potential targets parties must remain vigilant.

Operators of the GootLoader campaign are setting their sights on employees of accounting and law firms as part of a fresh onslaught of widespread cyberattacks to deploy malware on infected systems, an indication that the adversary is expanding its focus to other high-value targets. "GootLoader is a stealthy initial access malware, which after getting a foothold into the victim's computer system, infects the system with ransomware or other lethal malware," researchers from eSentire said in a report shared with The Hacker News.
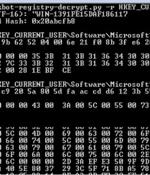
Cybersecurity researchers have decoded the mechanism by which the versatile Qakbot banking trojan handles the insertion of encrypted configuration data into the Windows Registry. Although mainly fashioned as an information-stealing malware, Qakbot has since shifted its goals and acquired new functionality to deliver post-compromise attack platforms such as Cobalt Strike Beacon, with the final objective of loading ransomware on infected machines.

The major players in the space were simply too large to facilitate a quick digital transformation, but the arrival of nimble start-ups and changing user habits have really led them to embrace digital banking. The move to online banking presents a larger attack surface for cybercriminals to exploit and attack.

ESET researchers took an in-depth look into the abuse of vulnerable kernel drivers. Among the various types of kernel drivers are "Software" drivers that provide specific, non-hardware related features like software debugging and diagnostics, system analysis, etc.

"These results demonstrate that while IT security threats have increased-primarily from the general hacking community and foreign governments-the ability to detect and remediate such threats has not increased at the same rate, leaving public sector organizations vulnerable," said Brandon Shopp, Group VP, Product Strategy, SolarWinds. State and local governments are significantly more likely than other public sector groups to be concerned about the threat of the general hacking community.

These investments empower organizations to provision enterprise workloads at edge locations in support of innovative edge use cases. Accordingly, a symbiotic edge and core to workload relationship is needed to enable workloads based at the core that support the edge, workloads based at the edge that support the edge, and workloads at the edge that support the core.