Security News > 2021 > October

The United Kingdom has revealed plans to invest £5 billion in bolstering national cybersecurity that includes creating a "Cyber Force" unit to perform retaliatory attacks. As the UK's Secretary of State for Defense Ben Wallace points out in an interview with The Telegraph, Britain isn't just looking to strengthen its stance against threats, but also to build up its capacity to launch retaliatory assaults.

Atom Silo, a newly spotted ransomware group, is targeting a recently patched and actively exploited Confluence Server and Data Center vulnerability to deploy their ransomware payloads. Ransomware gangs start targeting Confluence servers.

Europol has announced the arrest of two men in Ukraine, said to be members of a prolific ransomware operation that extorted victims with ransom demands ranging between €5 to €70 million. The international law enforcement operation was conducted in coordination with the FBI, the French police, and the Ukrainian National Police.

BBC R&D discovered it too didn't much like the way personal data was in the hands of the wrong people. You keep your personal data stored on an edge device you control.

Who, Me? Start your week with a warning about those temporary emergency hacks that all too often end up permanent in today's edition of Who, Me? Our story comes from "Gary" - for that is not his name - who worked for a firm that offered a variety of services to the UK banking sector. "Except it didn't," Gary told us, "Because after several fruitless months, the new shiny 'Big Red Firewall' still flatly refused to pass packets on two ports from one host to the other."

Dealing with a problem with the wrong toolset leads to reverse evolution - as we can see in the vulnerability management market, where tools are becoming more of a distraction to security professionals than the insightful guide to better security that they promise to be. Legacy vulnerability management tools flood security teams with long lists of community prioritized vulnerabilities - there were more than 15,000 vulnerabilities found only in 2020.
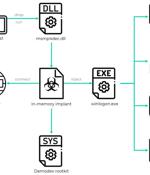
A formerly unknown Chinese-speaking threat actor has been linked to a long-standing evasive operation aimed at South East Asian targets as far back as July 2020 to deploy a kernel-mode rootkit on compromised Windows systems. Attacks mounted by the hacking group, dubbed GhostEmperor by Kaspersky, are also said to have used a "Sophisticated multi-stage malware framework" that allows for providing persistence and remote control over the targeted hosts.

A previously undocumented threat actor has been identified as behind a string of attacks targeting fuel, energy, and aviation production industries in Russia, the U.S., India, Nepal, Taiwan, and Japan with the goal of stealing data from compromised networks. "The group compromised a subsidiary and penetrated the target company's network through it. Trusted relationship attacks are rare today due to the complexity of their execution. Using this method [], the ChamelGang group was able to achieve its goal and steal data from the compromised network."

Like most, they initially turned toward the standard metrics used in cybersecurity, built around a "Mean Time to X" formula, where X indicates a specific milestone in the attack lifecycle. In order to better understand how considering SNR as well will service your SOC better, let's walk through three key shortcomings of Mean Time metrics.

The recent SolarWinds IT Trends Report found 49% of IT pro respondents perceive their organization's senior leaders or decision makers have a heightened awareness of risk exposure, believing it's not "If" but "When" they will be impacted by a risk factor. Here, we look at how this awareness represents a greater opportunity for IT pros to collaborate with senior leaders and help ensure better risk mitigation for businesses.