Security News

The real impact of the cybersecurity poverty line on small organizationsIn this Help Net Security interview, Brent Deterding, CISO at Afni, delves into the realities and myths surrounding the cybersecurity poverty line, exploring the role of budget, knowledge, and leadership. Cisco IOS XE zero-day exploited by attackers to deliver implantA previously unknown vulnerability affecting networking devices running Cisco IOS XE software is being exploited by a threat actor to take control of the devices and install an implant, Cisco Talos researchers have warned today.

Cisco has warned of a new zero-day flaw in IOS XE that has been actively exploited by an unknown threat actor to deploy a malicious Lua-based implant on susceptible devices. Tracked as...

Cisco disclosed a new high-severity zero-day today, actively exploited to deploy malicious implants on IOS XE devices compromised using the CVE-2023-20198 zero-day unveiled earlier this week. On Monday, Cisco disclosed that unauthenticated attackers have been exploiting the CVE-2023-20198 authentication bypass zero-day since at least September 18 to hack into IOS XE devices and create "Cisco tac admin" and "Cisco support."

More than 40,000 Cisco devices running the IOS XE operating system have been compromised after hackers exploited a recently disclosed maximum severity vulnerability tracked as CVE-2023-20198. Initial estimates of breached Cisco IOS XE devices were around 10,000 and the number started growing as security researchers scanned the internet for a more accurate figure.

A critical vulnerability tracked as CVE-2023-4966 in Citrix NetScaler ADC/Gateway devices has been actively exploited as a zero-day since late August, security researchers announced. A report from Mandiant disclosed that it found signs of CVE-2023-4966 being exploited in the wild since August for stealing authentication sessions and hijacking accounts.

Cisco Talos discovered a new critical zero-day vulnerability in the Web User Interface feature of Cisco IOS XE software that's currently being used in the wild. The vulnerability used to access the system and create those accounts is CVE-2023-20198; it received the highest Common Vulnerability Scoring System score of 10.

Attackers have exploited a recently disclosed critical zero-day bug to compromise and infect more than 10,000 Cisco IOS XE devices with malicious implants. According to threat intelligence company VulnCheck, the maximum severity vulnerability has been extensively exploited in attacks targeting Cisco IOS XE systems with the Web User Interface feature enabled, that also have the HTTP or HTTPS Server feature toggled on.
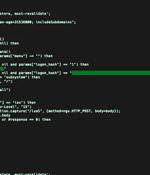
Cisco has warned of a critical, unpatched security flaw impacting IOS XE software that’s under active exploitation in the wild. Rooted in the web UI feature, the zero-day vulnerability is assigned...

A previously unknown vulnerability affecting networking devices running Cisco IOS XE software is being exploited by a threat actor to take control of the devices and install an implant, Cisco Talos researchers have warned today. CVE-2023-20198 is a privilege escalation vulnerability in the web UI feature of Cisco IOS XE software, which is installed on various Cisco controllers, switches, edge, branch and virtual routers.

Cisco warned admins today of a new and maximum severity zero-day vulnerability in its IOS XE Software that can let attackers gain full administrator privileges and take complete control of affected routers. "Cisco has identified active exploitation of a previously unknown vulnerability in the Web User Interface feature of Cisco IOS XE software when exposed to the internet or untrusted networks," the company revealed today.