Security News

Attackers have seized on vulnerabilities in these environments, creating more work and larger budgets for security teams. The hybrid workforce reality is causing greater concerns with data leakage, ransomware and attacks through remote access tools and cloud services.

Cybersecurity: Don't browse public Wi-Fi without a VPN. In the remote working age, we're all spending more time on public Wi-Fi than we're used to. When you're on public Wi-Fi, you should take some basic precautions to ensure your connection is protected.

While it is impossible to guarantee 100 percent protection on public Wi-Fi, there are certain measures that can be taken to significantly reduce the risk of cyberthreats over the network and most countries started forcing Wi-Fi providers to include cybersecurity protection along with the internet in order to make them comply with the law. Web filtering is considered to be an all-in-one package solution that protects users from cyber-threats while filtering the internet from unwanted content.

Don't browse on public Wi-Fi without a VPN. More than ever these days, people are working from home or on public Wi-Fi. With all that public Wi-Fi browsing, a VPN is the absolute base measure of security you should employ. These days, every company should use VPNs but it's also important for individuals to use a VPN whenever they're on public Wi-Fi. If you're in need of a high-quality VPN solution, you don't have to break the bank.

The global WiFi as a service market reached a value of $4.05 billion in 2021. Looking forward, the market is expected to reach $11.1 billion by 2027, exhibiting a CAGR of 17.5% during 2022-2027, according to ResearchAndMarkets.

Providing public Wi-Fi is a great service to offer your customers as it becomes more and more standard in today's society. According to recent statistics, there are about 410,000 public Wi-Fi hotspots in the United States alone, in public places such as parks, libraries, public transportation, and train stations.

Millions of home broadband Wi-Fi routers in the UK could be at risk because many internet users do not take basic security precautions that could protect them from online threats, a research from Broadband Genie has found. In a survey of 1,320 broadband users, it was discovered that 88% have never updated their router firmware and 84% have never changed their router admin password.

Millions of home broadband Wi-Fi routers in the UK could be at risk because many internet users do not take basic security precautions that could protect them from online threats, a research from Broadband Genie has found. In a survey of 1,320 broadband users, it was discovered that 88% have never updated their router firmware and 84% have never changed their router admin password.
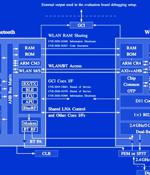
Cybersecurity researchers have demonstrated a new attack technique that makes it possible to leverage a device's Bluetooth component to directly extract network passwords and manipulate traffic on a Wi-Fi chip. The novel attacks work against the so-called "Combo chips," which are specialized chips that are equipped to handle different types of radio wave-based wireless communications, such as Wi-Fi, Bluetooth, and LTE. "We provide empirical evidence that coexistence, i.e., the coordination of cross-technology wireless transmissions, is an unexplored attack surface," a group of researchers from the Technical University of Darmstadt's Secure Mobile Networking Lab and the University of Brescia said in a new paper.

Researchers at the University of Darmstadt, Brescia, CNIT, and the Secure Mobile Networking Lab, have published a paper that proves it's possible to extract passwords and manipulate traffic on a WiFi chip by targeting a device's Bluetooth component. To exploit these vulnerabilities, the researchers first needed to perform code execution on either the Bluetooth or WiFi chip.