Security News

Ransomware payments hit new records in 2021 as cybercriminals increasingly turned to dark web leak sites where they pressured victims to pay up by threatening to release sensitive data, according to a research released from Unit 42 by Palo Alto Networks. The Conti ransomware group was responsible for the most activity, accounting for more than 1 in 5 of cases worked by Unit 42 consultants in 2021.

The breach, says the FTC, saw hackers make off with more than 20,000,000 plaintext email addresses and weakly-hashed passwords; millions of unencrypted names, physical addresses, and security questions-and-answers; more than 180,000 unencrypted SSNs; and, for tens of thousands of payment cards, the last four digits of the card plus the expiry date. Misrepresenting the steps it took to secure consumer accounts following security incidents.

SolarWinds warned customers of attacks targeting Internet-exposed Web Help Desk instances and advised removing them from publicly accessible infrastructure. "A SolarWinds customer reported an external attempted attack on their instance of Web Help Desk 12.7.5. The customer's endpoint detection and response system blocked the attack and alerted the customer to the issue," SolarWinds said.

Radware released report findings which underscore 2021 as the year of the web application attack. Between 2020 and 2021, the number of malicious web application requests climbed 88%, more than double the year-over-year growth rate in distributed denial-of-service attacks, which were up 37% over 2020.
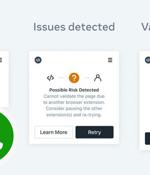
Meta Platforms' WhatsApp and Cloudflare have banded together for a new initiative called Code Verify to validate the authenticity of the messaging service's web app on desktop computers. Available in the form of a Chrome and Edge browser extension, the open-source add-on is designed to "Automatically verif[y] the authenticity of the WhatsApp Web code being served to your browser," Facebook said in a statement.

WhatsApp and Cloudflare have teamed up to provide desktop users of WhatsApp's web client with a browser extension called Code Verify that checks the integrity of the software running in their browser. The Meta-owned biz would like to add more security to its web client, because web security differs from native app security and WhatsApp is seeing more web usage.

The particular provision requires web browsers like Chrome, Safari, and Firefox to accept QWACs, which practically compels browser developers and security advocates to ease their security stance. TLS certificates are vital for the online exchange of sensitive information with websites such as passwords, sensitive uploads, or payment details.

While it is impossible to guarantee 100 percent protection on public Wi-Fi, there are certain measures that can be taken to significantly reduce the risk of cyberthreats over the network and most countries started forcing Wi-Fi providers to include cybersecurity protection along with the internet in order to make them comply with the law. Web filtering is considered to be an all-in-one package solution that protects users from cyber-threats while filtering the internet from unwanted content.
Why is a web filtering important and what are the main features necessary for MSPs? Managed service providers have been struggling with finding the right web filtering solutions. Web filtering is necessary for businesses because it prevents the staff from accessing malicious and harmful content while using the corporate network or while working from home, besides offering other advantages like monitoring their performance and keeping it to the maximum to ensure productivity.

A special law enforcement operation undertaken by Russia has led to the seizure and shutdown of four online bazaars that specialized in the theft and sales of stolen credit cards, as the government continues to take active measures against harboring cybercriminals on its territory. Ferum Shop, active since October 2013, made as much as $256 million in Bitcoin from stolen card sales, accounting for nearly 17% of the stolen credit card market.