Security News

The Cybersecurity and Infrastructure Security Agency has added nine more security flaws to its list of actively exploited bugs, including a VMware privilege escalation flaw and a Google Chrome zero-day that could be used for remote code execution. A Chrome zero-day was also included in CISA's Known Exploited Vulnerabilities catalog, a bug tracked as CVE-2022-1364 and allowing remote code execution due to a V8 type confusion weakness.

Cloud computing and virtualization technology firm VMWare on Thursday rolled out an update to resolve a critical security flaw in its Cloud Director product that could be weaponized to launch remote code execution attacks. "An authenticated, high privileged malicious actor with network access to the VMware Cloud Director tenant or provider may be able to exploit a remote code execution vulnerability to gain access to the server," VMware said in an advisory.

A week after VMware released patches to remediate eight security vulnerabilities in VMware Workspace ONE Access, threat actors have begun to actively exploit one of the critical flaws in the wild. Tracked as CVE-2022-22954, the critical issue relates to a remote code execution vulnerability that stems from server-side template injection in VMware Workspace ONE Access and Identity Manager.

Cyber crooks have begun exploiting CVE-2022-22954, a RCE vulnerability in VMware Workspace ONE Access and Identity Manager, to deliver cryptominers onto vulnerable systems. CVE-2022-22954 is, in effect, a server-side template injection vulnerability that can be triggered by a malicious actor with network access to achieve remote code execution.

A proof-of-concept exploit has been released online for the VMware CVE-2022-22954 remote code execution vulnerability, already being used in active attacks that infect servers with coin miners. The vulnerability is a critical remote code execution impacting VMware Workspace ONE Access and VMware Identity Manager, two widely used software products.

A proof-of-concept exploit has been released online for the VMware CVE-2022-22954 remote code execution vulnerability, already being used in active attacks that infect servers with coin miners. The vulnerability is a critical remote code execution impacting VMware Workspace ONE Access and VMware Identity Manager, two widely used software products.

VMware has released security updates to patch eight vulnerabilities spanning its products, some of which could be exploited to launch remote code execution attacks. Credited with reporting all the vulnerabilities is Steven Seeley of Qihoo 360 Vulnerability Research Institute.

VMware has warned customers to immediately patch critical vulnerabilities in multiple products that threat actors could use to launch remote code execution attacks. "This critical vulnerability should be patched or mitigated immediately per the instructions in VMSA-2021-0011. The ramifications of this vulnerability are serious," VMware warned on Wednesday.

VMware has published security updates for the critical remote code execution vulnerability known as Spring4Shell, which impacts several of its cloud computing and virtualization products. A list of VMware products affected by Spring4Shell is available in an adivsory from the company.
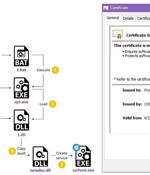
A Chinese advanced persistent threat tracked as Deep Panda has been observed exploiting the Log4Shell vulnerability in VMware Horizon servers to deploy a backdoor and a novel rootkit on infected machines with the goal of stealing sensitive data. Cybersecurity firm CrowdStrike, which assigned the panda-themed name to the group all the way back in July 2014, called it "One of the most advanced Chinese nation-state cyber intrusion groups."