Security News
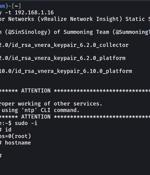
Proof-of-concept exploit code has been made available for a recently disclosed and patched critical flaw impacting VMware Aria Operations for Networks. "A malicious actor with network access to Aria Operations for Networks could bypass SSH authentication to gain access to the Aria Operations for Networks CLI," VMware said earlier this week.

Proof-of-concept exploit code has been released for a critical SSH authentication bypass vulnerability in VMware's Aria Operations for Networks analysis tool.Today, VMware confirmed that CVE-2023-34039 exploit code has been published online, two days after disclosing the critical security bug.

North Korean state-sponsored hackers have uploaded malicious packages to the PyPI repository, camouflaging one of them as a VMware vSphere connector module named vConnector. The packages were uploaded at the beginning of August, with one named VMConnect targeting IT professionals seeking virtualization tools.

VMware Aria Operations for Networks is vulnerable to a critical severity authentication bypass flaw that could allow remote attackers to bypass SSH authentication and access private endpoints. VMware Aria is a suite for managing and monitoring virtualized environments and hybrid clouds, enabling IT automation, log management, analytics generation, network visibility, security and capacity planning, and full-scope operations management.

VMware has patched one critical and one high-severity vulnerability in Aria Operations for Networks, its popular enterprise network monitoring tool. It could allow an attacker with network access to Aria Operations for Networks to bypass SSH authentication to gain access to the Aria Operations for Networks command-line interface.

VMware has released software updates to correct two security vulnerabilities in Aria Operations for Networks that could be potentially exploited to bypass authentication and gain remote code execution."A malicious actor with network access to Aria Operations for Networks could bypass SSH authentication to gain access to the Aria Operations for Networks CLI," the company said in an advisory.

Explore enterprise applications and infrastructure, AI, tools for the remote workforce, machine learning, and more from VMware Explore 2023. VMware made several announcements related to new cloud, edge and machine learning services on August 22 at VMware Explore held in Las Vegas.

The Monti ransomware gang has returned, after a two-month break from publishing victims on their data leak site, using a new Linux locker to target VMware ESXi servers, legal, and government organizations. Researchers at Trend Micro analyzing the new encryption tool from Monti found that it has "Significant deviations from its other Linux-based predecessors."

An unfixed hardcoded encryption key flaw in Dell's Compellent Integration Tools for VMware (CITV) allows attackers to decrypt stored vCenter admin credentials and retrieve the cleartext password. [...]

Ransomware gangs continue to prioritize targeting VMware ESXi servers, with almost every active ransomware gang creating custom Linux encryptors for this purpose. Hospitals run by Prospect Medical Holdings were also impacted this week by a ransomware attack on the parent company.