Security News

A hybrid espionage/influence campaign conducted by the Russian threat group 'UNC5812' has been uncovered, targeting Ukrainian military recruits with Windows and Android malware. [...]

A suspected Russian hybrid espionage and influence operation has been observed delivering a mix of Windows and Android malware to target the Ukrainian military under the Telegram persona Civil...
The Computer Emergency Response Team of Ukraine (CERT-UA) has detailed a new malicious email campaign targeting government agencies, enterprises, and military entities. "The messages exploit the...
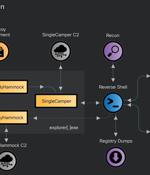
The Russian threat actor known as RomCom has been linked to a new wave of cyber attacks aimed at Ukrainian government agencies and unknown Polish entities since at least late 2023. The intrusions...

A group of pro-Ukrainian hacktivists has claimed responsibility for the September breach of Russian security company Doctor Web (Dr.Web). [...]

Ukraine has claimed responsibility for a cyber attack that targeted Russia state media company VGTRK and disrupted its operations, according to reports from Bloomberg and Reuters. The incident...

Ukrainian national Mark Sokolovsky has pleaded guilty to his involvement in the Raccoon Stealer malware-as-a-service (MaaS) cybercrime operation. [...]

Forget about your love life too, no dating apps until the war is over Russia's Ministry of Internal Affairs is warning residents of under-siege regions to switch off home surveillance systems and...

A coalition of law enforcement agencies coordinated by the U.K. National Crime Agency (NCA) has led to the arrest and extradition of a Belarussian and Ukrainian dual-national believed to be...

The Computer Emergency Response Team of Ukraine has alerted of a spear-phishing campaign targeting a scientific research institution in the country with malware known as HATVIBE and CHERRYSPY. The agency attributed the attack to a threat actor it tracks under the name UAC-0063, which was previously observed targeting various government entities to gather sensitive information using keyloggers and backdoors. Opening the document and enabling macros results in the execution of an encoded HTML Application named HATVIBE, which sets up persistence on the host using a scheduled task and paves the way for a Python backdoor codenamed CHERRYSPY, which is capable of running commands issued by a remote server.