Security News

A recently discovered worm that researchers call LittleDrifter has been spreading over USB drives infecting systems in multiple countries as part of a campaign from the Gamaredon state-sponsored espionage group. Malware researchers saw indications of compromise in the United States, Ukraine, Germany, Vietnam, Poland, Chile, and Hong Kong, which suggests that the threat group lost control of LittleDrifter, which reached unintended targets.

Mandiant, a cybersecurity company owned by Google, has revealed the details of a 2022 cyberattack run by Russian threat actor Sandworm. The threat group then accessed the OT environment "Through a hypervisor that hosted a Supervisory Control And Data Acquisition management instance for the victim's substation environment," according to Mandiant researchers, who stated the attacker potentially had access to the SCADA system for up to three months.

The notorious Russian hackers known as Sandworm targeted an electrical substation in Ukraine last year, causing a brief power outage in October 2022. "The actor first used OT-level living-off-the-land techniques to likely trip the victim's substation circuit breakers, causing an unplanned power outage that coincided with mass missile strikes on critical infrastructure across Ukraine," the company said.

The International Committee of the Red Cross, the humanitarian protection organization responsible for promoting international law, has set out eight rules for hacktivists and another four for states to discourage civilian involvement in cyberattacks against other countries. The rate at which civilians are becoming involved in international conflicts has been described as "a worrying trend" by the ICRC - a phenomenon exacerbated by the ongoing war in Ukraine, which has seen for the first time conflict taking place in both the physical and digital space concurrently.

"Their primary objectives were to identify which evidence of Russian war crimes and exercise control over potential ground-deployed spies have our law enforcement teams," states the report [PDF], which was released on Monday. Intruders linked to Russia's Federal Security Service, Main Intelligence Directorate, and Foreign Intelligence Service also sought out material that could be used in criminal proceedings against Russian spies, other specific individuals, institutions, and organizations "Potentially leading to sanctions or other actions," the SSSCIP reports.
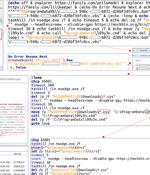
The Computer Emergency Response Team of Ukraine on Tuesday said it thwarted a cyber attack against an unnamed critical energy infrastructure facility in the country. "Visiting the link will download a ZIP archive containing three JPG images and a BAT file 'weblinks.cmd' to the victim's computer," CERT-UA said, attributing it to the Russian threat actor known as APT28.

Chinese companies, including state-owned defense companies, are evading tech sanctions and fueling Moscow's war in Ukraine, according to a US report released on Thursday. "Beijing is pursuing a variety of economic support mechanisms for Russia that mitigate both the impact of Western sanctions and export controls," states the report.

Ukrainian cops have disrupted a massive bot farm with more than 100 operators allegedly spreading fake news about the Russian invasion, leaking personal information belonging to Ukrainian citizens, and instigating fraud schemes. "The Cyber Police established that the attackers used special equipment and software to register thousands of bot accounts in various social networks and subsequently launch advertisements that violated the norms and legislation of Ukraine," according to machine translation of the news alert issued by the police.

The Cyber ??Police Department of the National Police of Ukraine dismantled another massive bot farm linked to more than 100 individuals after searches at almost two dozen locations. Since the start of the war in Ukraine, Russian threat actors have been involved in disinformation campaigns targeting Ukraine and have invested in Ukraine-based bot farms.
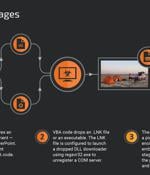
Government entities, military organizations, and civilian users in Ukraine and Poland have been targeted as part of a series of campaigns designed to steal sensitive data and gain persistent remote access to the infected systems. The intrusion set, which stretches from April 2022 to July 2023, leverages phishing lures and decoy documents to deploy a downloader malware called PicassoLoader, which acts as a conduit to launch Cobalt Strike Beacon and njRAT. "The attacks used a multistage infection chain initiated with malicious Microsoft Office documents, most commonly using Microsoft Excel and PowerPoint file formats," Cisco Talos researcher Vanja Svajcer said in a new report.