Security News

Ukraine blames Belarus for PC-wiping 'ransomware' that has no recovery method and nukes target boxen
After last week's website defacements, Ukraine is now being targeted by boot record-wiping malware that looks like ransomware but with one crucial difference: there's no recovery method. The malware itself wipes the target Windows system's master boot record, rendering it inoperable, and its main executable is "Often" named stage1.

In the wake of last week's attention-grabbing defacements of many Ukrainian government websites, Microsoft researchers have revealed evidence of a malware operation targeting multiple organizations in Ukraine, deploying what seems to be ransomware but is actually Master Boot Records wiper malware. Late on Saturday, Microsoft shared information and IOCs related to a malware campaing targeting Ukrainian organizations.

Microsoft is warning of destructive data-wiping malware disguised as ransomware being used in attacks against multiple organizations in Ukraine. Starting January 13th, Microsoft detected the new attacks that combined a destructive MBRLocker with a data-corrupting malware used to destroy the victim's data intentionally.

Ukrainian police authorities have nabbed five members of a gang that's believed to have helped orchestrate attacks against more than 50 companies across Europe and the U.S and caused losses to the tune of more than $1 million. The Cyber Police of the National Police of Ukraine said the group offered a "Hacker service" that enabled financially motivated crime syndicates to send phishing emails containing file-encrypted malware to lock confidential data pertaining to its victims, demanding that the targets pay cryptocurrency ransoms in return for restoring access to the files.

A "Massive" cyber attack on Ukraine caught the world's eye this morning as the country's foreign ministry said its website, among others, had been taken down by unidentified hackers. Ukraine itself held off on attribution, with a foreign ministry spokesman telling the Reuters newswire it was too early to say who was responsible - but adding Russia has done similar things in the past.

Both Russia and Ukraine are preparing for military operations in cyberspace.

Europol, the European Union's premier law enforcement agency, has announced the arrest of a third Romanian national for his role as a ransomware affiliate suspected of hacking high-profile organizations and companies and stealing large volumes of sensitive data. It's not currently known which ransomware gang the suspect was working with, but the development comes a little over a month after Romanian authorities arrested two affiliates of the REvil ransomware family, who are believed to have orchestrated no fewer than 5,000 ransomware attacks and extorted close to $600,000 from victims.

Ukrainian law enforcement arrested 51 suspects believed to have been selling stolen personal data on hacking forums belonging to hundreds of millions worldwide, including Ukraine, the US, and Europe. "As a result of the operation, about 100 databases of personal data relevant for 2020-2021 were seized," the Cyberpolice Department of the National Police of Ukraine said.

The Security Service of Ukraine has arrested five members of the international 'Phoenix' hacking group who specialize in the remote hacking of mobile devices. The goal of 'Phoenix' was to gain remote access to the accounts of mobile device users and then monetize them by hijacking their e-payment or bank accounts or selling their private information to third parties.
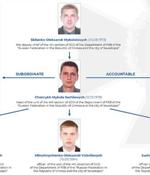
Ukraine's premier law enforcement and counterintelligence agency on Thursday disclosed the real identities of five individuals allegedly involved in digital intrusions attributed to a cyber-espionage group named Gamaredon, linking the members to Russia's Federal Security Service. Calling the hacker group "An FSB special project, which specifically targeted Ukraine," the Security Service of Ukraine said the perpetrators "Are officers of the 'Crimean' FSB and traitors who defected to the enemy during the occupation of the peninsula in 2014.".