Security News

The ten most prolific Android mobile banking trojans target 639 financial applications that collectively have over one billion downloads on the Google Play Store. Mobile banking trojans hide behind seemingly benign apps like productivity tools and games and commonly sneak into the Google Play Store, Android's official app store.

Kaspersky's quarterly report on mobile malware distribution notes a downward trend that started in late 2020. Despite the overall demise in malware volumes, the security company reports a spike in trojan distribution, including generic trojans, banking trojans, and spyware.

A newly discovered and complex remote access trojan is spreading via malicious email campaigns using COVID-19 lures and includes numerous features to evade analysis or detection by researchers, Proofpoint has found. Dubbed Nerbian RAT, the novel malware variant is written in the OS-agnostic Go programming language and "Utilizes significant anti-analysis and anti-reversing capabilities", according to a Proofpoint blog post published Wednesday.
A new set of trojanized apps spread via the Google Play Store has been observed distributing the notorious Joker malware on compromised Android devices. Despite continued attempts on the part of Google to scale up its defenses, the apps have been continually iterated to search for gaps and slip into the app store undetected.
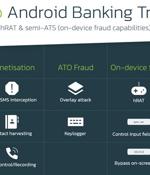
A number of rogue Android apps that have been cumulatively installed from the official Google Play Store more than 50,000 times are being used to target banks and other financial entities. Like other Android banking trojans, the rogue apps are nothing more than droppers, whose primary function is to deploy the malicious payload embedded within them.
As many as seven malicious Android apps discovered on the Google Play Store masqueraded as antivirus solutions to deploy a banking trojan called SharkBot. "SharkBot steals credentials and banking information," Check Point researchers Alex Shamshur and Raman Ladutska said in a report shared with The Hacker News.

Remote Access Trojan adds ransomware and DDoS attacks to usual bag of tricks. The Remote Access Trojan, or RAT for short, is a powerful tool among cybercriminals as it allows them to fully access and control a compromised computer or device to steal data or launch additional attacks.

A threat actor is exploiting vulnerable on-prem Microsoft Exchange servers and using hijacked email threads to deliver the IceID trojan without triggering email security solutions. The threat actor - believe to be an initial access broker - compromises vulnerable on-prem Microsoft Exchange servers and existing email accounts, then hijacks email threads by replying to them.

The trojanized Craftsart Cartoon Photo Tools app is available in the official Android app store, but it's actually spyware capable of stealing any and all information from victims' social-media accounts. A popular mobile app in the official Google Play store called "Craftsart Cartoon Photo Tools" has racked up more than 100,000 installs - but unfortunately for the app's enthusiasts, it contains a version of the Facestealer Android malware.

Security researchers tracking the mobile app ecosystem have noticed a recent spike in trojan infiltration on the Google Play Store, with one of the apps having over 500,000 installs and available to download. Most of these apps belong to a family of trojan malware used in various scams, resulting in financial losses and also loss of sensitive personal information. The threats discovered on the Play Store by Dr. Web's analysts include cryptocurrency management apps, social benefit aid tools, Gasprom investment clones, photo editors, and a launcher themed after iOS 15.