Security News

NCC Group's Global Threat Intelligence team, in its monthly cybersecurity Threat Pulse, noted there were 240 ransomware attacks in February 2023 - a 45% increase from the record-high number of attacks in January. The NCC Group also reported that ransomware LockBit 3.0 was the leading arrowhead, with the eponymous threat group having launched 129, or 54%, of ransomware salvos last month, including an attack on the U.K.'s Royal Mail.

The report delves into the efficacy of different security controls, the most concerning threats as tested by organizations worldwide, and top cybersecurity best practices for 2023. Many organizations are testing for trending threats.

Why? Bad actors know that SMEs typically have a smaller security budget, less infosec manpower, and possibly weak or missing security controls to protect their data and infrastructure. The good news is you don't have to create your security strategy from scratch.

US Cyber Command operators have confirmed they carried out an online defensive mission in Albania, in response to last year's cyber attacks against the local government. Over the course of the three-month deployment, Cyber National Mission Force troops worked with their Albanian counterparts to hunt for cyber threats and identify vulnerabilities on networks in the NATO country.

Between January 2021 and October 2022, the EU Agency for Cybersecurity analyzed and mapped the cyber threats faced by the transport sector, identifying prime threats, analyzing incidents, assessing threat actors, analyzing their motivations, and introducing major trends for each sub-sector, thereby providing new insights. EU Agency for Cybersecurity Executive Director, Juhan Lepassaar, stated that "Transport is a key sector of our economy that we depend on in both our personal and professional lives. Understanding the distribution of cyber threats, motivations, trends and patterns as well as their potential impact, is crucial if we want to improve the cybersecurity of the critical infrastructures involved."

Configure Active Directory securely with LDAP signing and LDAPS requirements, regularly rotate the KRBTGT password and use group-managed service accounts to rotate service account credentials. Enable multi-factor authentication and a strong password policy, augmented by solutions such as Specops Password Policy.
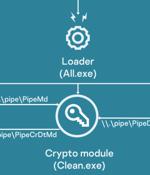
Amid the ongoing war between Russia and Ukraine, government, agriculture, and transportation organizations located in Donetsk, Lugansk, and Crimea have been attacked as part of an active campaign that drops a previously unseen, modular framework dubbed CommonMagic. "Although the initial vector of compromise is unclear, the details of the next stage imply the use of spear phishing or similar methods," Kaspersky said in a new report.

Why? Bad actors know that SMEs typically have a smaller security budget, less infosec manpower, and possibly weak or missing security controls to protect their data and infrastructure. The good news is you don't have to create your security strategy from scratch.

The rise of QR scan scams: Since October 2022, HP has seen almost daily QR code "Scan scam" campaigns. These scams trick users into scanning QR codes from their PCs using their mobile devices - potentially to take advantage of weaker phishing protection and detection on such devices.

The guide, "Protection from web-borne threats starts with Browser Security Platform," details the characteristics and the capabilities of a potential solution, and explains how it compares to other security solutions and why it is needed. The guide calls for the recognition of an emerging security solution category, Browser Security Platform, which provides visibility into the browser's application layer.