Security News
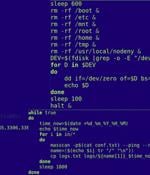
The Computer Emergency Response Team of Ukraine (CERT-UA) has revealed that threat actors "interfered" with at least 11 telecommunication service providers in the country between May and September...

A newly discovered campaign dubbed "Stayin' Alive" has been targeting government organizations and telecommunication service providers across Asia since 2021, using a wide variety of "Disposable" malware to evade detection. The attacks appear to originate from the Chinese espionage actor known as 'ToddyCat,' which relies on spear-phishing messages carrying malicious attachments to load a variety of malware loaders and backdoors.
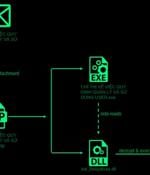
High-profile government and telecom entities in Asia have been targeted as part of an ongoing campaign since 2021 that's designed to deploy basic backdoors and loaders for delivering next-stage...
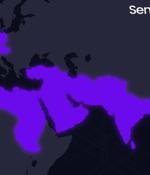
A previously undocumented threat actor dubbed Sandman has been attributed to a set of cyber attacks targeting telecommunic koation providers in the Middle East, Western Europe, and the South Asian...

Researchers have unearthed new backdoors leveraged to maintain long-term access in the networks of telecom firms in the Middle East. HTTPSnoop and PipeSnoop - as the two implants have been dubbed by Cisco Talos researchers - have been disguised as components of Palo Alto Networks' Cortex XDR solution.

New malware named HTTPSnoop and PipeSnoop are used in cyberattacks on telecommunication service providers in the Middle East, allowing threat actors to remotely execute commands on infected devices. The HTTPSnoop malware interfaces with Windows HTTP kernel drivers and devices to execute content on the infected endpoint based on specific HTTP(S) URLs, and the PipeSnoop accepts and executes arbitrary shellcode from a named pipe.

Telecommunication service providers in the Middle East are the target of a new intrusion set dubbed ShroudedSnooper that employs a stealthy backdoor called HTTPSnoop. "HTTPSnoop is a simple, yet effective, backdoor that consists of novel techniques to interface with Windows HTTP kernel drivers and devices to listen to incoming requests for specific HTTP(S) URLs and execute that content on the infected endpoint," Cisco Talos said in a report shared with The Hacker News.
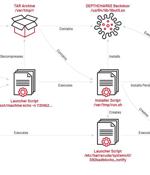
A suspected Chinese-nexus hacking group exploited a recently disclosed zero-day flaw in Barracuda Networks Email Security Gateway appliances to breach government, military, defense and aerospace, high-tech industry, and telecom sectors as part of a global espionage campaign. What's more, FOXTROT shares overlaps with an open-source rootkit called Reptile, which has been extensively used by multiple Chinese hacking crews in recent months.

Considering the phenomenal increase in mobile and IoT devices, data traffic subscribers, and SIM connections, how have the security challenges evolved for telecom providers? Regardless of the security of the network connection, the consumer should be provided with the protection they need to keep them and their data safe.

The malware "Possesses the ability to steal information from various browsers, enabling the exfiltration of sensitive data, while also incorporating different modules for carrying out ransomware activities," Zscaler researchers Shatak Jain and Gurkirat Singh said in a recent analysis. Following a successful breach, the malicious binary is used as a conduit to set up persistence, perform the actual browser update, and also drop a stealer capable of covertly harvesting sensitive information and encrypting the stolen files, leaving the victims at risk of potential data loss, exposure, or even the sale of their valuable data.