Security News

Telecommunications and IT service providers in the Middle East and Asia are being targeted by a previously undocumented Chinese-speaking threat group dubbed WIP19. "Almost all operations performed by the threat actor were completed in a 'hands-on keyboard' fashion, during an interactive session with compromised machines," SentinelOne researchers Joey Chen and Amitai Ben Shushan Ehrlich said in a report this week.
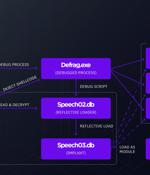
The cybersecurity firm codenamed the group Metador in reference to a string "I am meta" in one of their malware samples and because of Spanish-language responses from the command-and-control servers. The threat actor is said to have primarily focused on the development of cross-platform malware in its pursuit of espionage aims.

The Russian state-sponsored hacking group known as Sandworm has been observed masquerading as telecommunication providers to target Ukrainian entities with malware. Sandworm is a state-backed threat actor attributed by the US government as part of the Russian GRU foreign military intelligence service.

US mobile carriers know a lot about where their customers are located, and according to letters sent to the Federal Communications Commission, they routinely store such data for years, willingly hand it over to law enforcement if served a proper subpoena, and say users can't opt out. News that cellular carriers are storing sensitive location data isn't surprising given previous actions taken against AT&T, Verizon, T-Mobile US and Sprint by the FCC in 2020 for selling location data to third parties.

The US Federal Communications Commission notified Congress on Friday that the cost to rip and replace equipment kit from Huawei and ZTE installed at US telcos is more than $3 billion higher than funding allocated for the program. FCC chair Jessica Rosenworcel wrote to explain the situation, which arose from the USA's desire to remove Chinese comms kit at local carriers in the name of national security.

State-sponsored Chinese attackers are actively exploiting old vulnerabilities to "Establish a broad network of compromised infrastructure" then using it to attack telcos and network services providers. The advisory states that network devices are the target of this campaign and lists 16 flaws - some dating back to 2017 and none more recent than April 2021 - that the three agencies rate as the most frequently exploited.

Several US federal agencies today revealed that Chinese-backed threat actors have targeted and compromised major telecommunications companies and network service providers to steal credentials and harvest data. "Upon gaining an initial foothold into a telecommunications organization or network service provider, PRC state-sponsored cyber actors have identified critical users and infrastructure including systems critical to maintaining the security of authentication, authorization, and accounting," the advisory explains.

A previously unknown and financially motivated hacking group is impersonating a Russian agency in a phishing campaign targeting entities in Eastern European countries. The phishing emails pretend to come from the Russian Government's Federal Bailiffs Service and are written in the Russian language, with the recipients being telecommunication service providers and industrial firms in Lithuania, Estonia, and Russia.

Attackers targeting telcos across the Middle East and Asia for the past six months are linked to Iranian state-sponsored hackers, according to researchers. Though the identity of attackers also is unconfirmed, they potentially could be linked to the Iranian group Seedworm, aka MuddyWater or TEMP.Zagros, researchers said.

The Iranian state-supported APT known as 'Lyceum' targeted ISPs and telecommunication service providers in the Middle East and Africa between July and October 2021. Apart from Israel, which is permanently in the crosshairs of Iranian hackers, researchers have spotted Lyceum backdoor malware attacks in Morocco, Tunisia, and Saudi Arabia.