Security News

As organizations navigate the complexities of hybrid work arrangements and the gradual return to the office, the cybersecurity threat landscape has become increasingly challenging, with issues such as the proliferation of personal devices, the expansion of remote access points, and the potential for security gaps between in-office and remote environments. Issues such as the proliferation of personal devices, the expansion of remote access points, and the potential for security gaps between in-office and remote environments have compounded these challenges.

Your profile can be used to present content that appears more relevant based on your possible interests, such as by adapting the order in which content is shown to you, so that it is even easier for you to find content that matches your interests. Content presented to you on this service can be based on your content personalisation profiles, which can reflect your activity on this or other services, possible interests and personal aspects.

Your profile can be used to present content that appears more relevant based on your possible interests, such as by adapting the order in which content is shown to you, so that it is even easier for you to find content that matches your interests. Content presented to you on this service can be based on your content personalisation profiles, which can reflect your activity on this or other services, possible interests and personal aspects.
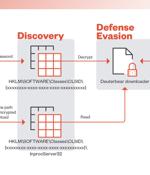
Technology, research, and government sectors in the Asia-Pacific region have been targeted by a threat actor called BlackTech as part of a recent cyber attack wave. The intrusions pave the way for...

Your profile can be used to present content that appears more relevant based on your possible interests, such as by adapting the order in which content is shown to you, so that it is even easier for you to find content that matches your interests. Content presented to you on this service can be based on your content personalisation profiles, which can reflect your activity on this or other services, possible interests and personal aspects.

31% of women in tech are considering leaving their organization over the next 12 months due foremost to poor management, followed by a lack of training and a desire for better compensation, according to Skillsoft. The survey yielded more than 500 complete responses from women who work in the tech industry, at tech organizations or companies, and in tech roles.

APAC regional B2B enterprises will need to consider their levels of investment in a number of technologies and integrating new tools now to prepare for and adapt to the coming changes. The B2B Futures: The View From 2030 report argues four key "Seismic" trends are coming to B2B:. Jake Hird, vice president of strategy, Merkle B2B - APAC, told TechRepublic B2B enterprises in the region will need to respond with investment in technologies including IoT, AI, data analytics and blockchain to ensure they adapt to these shifts hitting their businesses and markets.

Zero-day exploits targeting enterprise-specific software and appliances are now outpacing zero-day bugs overall, according to Google's threat hunting teams. While 61 of the 97 zero-days affected end-user products last year, this number isn't increasing as rapidly as its enterprise counterparts.

Innovation fuels the technology industry, but it comes at a cost. Certain technology sub-sectors like software companies and infrastructure providers have complex supply chains, making it challenging to ensure the security of all components and services.

In what was originally being called a serious IT outage at the end of last week, the union confirmed to The Register today that the incident is now being treated as an attack, the full extent of which is still being assessed. The CWU told us on March 22 that its email services weren't working and that it has engaged third-party cybersecurity experts who have been on site since 0900 UTC on March 21.