Security News

Lax policies for package naming on Microsoft's PowerShell Gallery code repository allow threat actors to perform typosquatting attacks, spoof popular packages and potentially lay the ground for massive supply chain attacks. PowerShell Gallery is a Microsoft-run online repository of packages uploaded by the wider PowerShell community, hosting a large number of scripts and cmdlet modules for various purposes.

In recent years, ransomware groups have evolved their tactics to not only encrypt data but also exfiltrate it, making it a double-edged weapon for extortion. The rise of data extortion ransomware has coincided with a dramatic increase in both the number of groups active and the number of attacks against organizations.
Active flaws in the PowerShell Gallery could be weaponized by threat actors to pull off supply chain attacks against the registry's users. "These flaws make typosquatting attacks inevitable in this registry, while also making it extremely difficult for users to identify the true owner of a package," Aqua security researchers Mor Weinberger, Yakir Kadkoda, and Ilay Goldman said in a report shared with The Hacker News.

The software supply chain encompasses the entire lifecycle of a software product, from its conception and development to its distribution and deployment. One of the key challenges in the software supply chain is the growing reliance on third-party components and dependencies, especially in open-source software.
Cybersecurity researchers said they have discovered what they say is the first open-source software supply chain attacks specifically targeting the banking sector. "These attacks showcased advanced techniques, including targeting specific components in web assets of the victim bank by attaching malicious functionalities to it," Checkmarx said in a report published last week.

In this Help Net Security video, Marc Gaffan, CEO at IONIX, discusses how businesses' biggest cybersecurity mistake is not protecting the full external attack surface that continues to expand to include a businesses' entire digital supply chain. This is driven by third-party vendors, cloud, shadow IT, and managed services like SaaS applications.
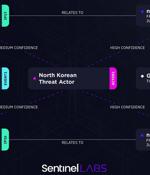
An analysis of the indicators of compromise associated with the JumpCloud hack has uncovered evidence pointing to the involvement of North Korean state-sponsored groups, in a style that's reminiscent of the supply chain attack targeting 3CX. The findings come from SentinelOne, which mapped out the infrastructure pertaining to the intrusion to uncover underlying patterns. "The North Korean threat actors demonstrate a high level of creativity and strategic awareness in their targeting strategies," SentinelOne security researcher Tom Hegel told The Hacker News.

Supply chain executives significantly overestimate stakeholder trust in their supply chain capabilities and intentions, according to Deloitte. Of more than 1,000 executives from large global organizations surveyed, 89% on average who self-identified as leading suppliers said customers trust their supply chain operations, compared to just 68% on average of roughly 500 customers who said the same.

A critical design flaw in the Google Cloud Build service discovered by cloud security firm Orca Security can let attackers escalate privileges, providing them with almost nearly-full and unauthorized access to Google Artifact Registry code repositories. Dubbed Bad.Build, this flaw could enable the threat actors to impersonate the service account for the Google Cloud Build managed continuous integration and delivery service to run API calls against the artifact registry and take control over application images.

Decades ago, Tony Turner, CEO of Opswright and author of Software Transparency: Supply Chain Security in an Era of a Software-Driven Society, faced an SQL Slammer worm. During his 25-year career in supply chain security and product security, he became an expert in engineering, security, and product design and he even served as the VP of R&D at Fortress.