Security News

4-year trial is second major initiative this year that clamps down on 'illegal immigrants' Foreigners in Moscow will now be subject to a new experimental law that affords the state enhanced...

Fourth time’s the harm? Gravy Analytics has been sued yet again for allegedly failing to safeguard its vast stores of personal data, which are now feared stolen. And by personal data we mean...

A lost, stolen, or compromised smartphone today means we are in serious trouble. Most people have everything related to their personal and professional lives stored on their phones, a fact that...

Plus: UK man charged with compromising firms for stock secrets; ransomware actor foils self; and more Infosec In Brief Put away that screwdriver and USB charging cable – the latest way to steal a...

Chinese upstarts are selling smartphone motherboards - and kit to run and manage them at scale - to operators of outfits that use them to commit various scams and crimes, according to an undercover investigation by state television broadcaster China Central Television revealed late last week. The report shows what appear to be chassis filled with 20 smartphone motherboards each, wired to a monitor that displays the screens of all 20 units.
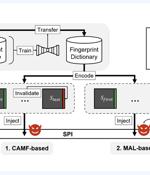
Researchers have discovered an inexpensive attack technique that could be leveraged to brute-force fingerprints on smartphones to bypass user authentication and seize control of the devices. The approach, dubbed BrutePrint, bypasses limits put in place to counter failed biometric authentication attempts by weaponizing two zero-day vulnerabilities in the smartphone fingerprint authentication framework.

1, How fast do people need to access the motion detectors to make them universally usefull. 2, How fast do attackers need to access the motion detectors to gleen sufficient information to re-constitute a known persons speech.

At its Ignite 2022 event last month, Microsoft announced general availability of Azure Active Director certificate-based authentication, addressing a component the Biden Administration's executive order last year to strengthen the US's cybersecurity. Microsoft is now offering a public preview of Azure AD CBA on devices running Apple's iOS and Android that uses certificates on Yubico's YubiKey hardware security key.

At the Samsung Developer Conference 2022, the company also discussed its plans for personalized experiences, security and privacy. The post Samsung unveils latest features for smartphones, smart...

A pair of preprint papers from Mordechai Guri, head of R&D at Ben-Gurion University's Cyber Security Research Labs, detail new methods for transmitting data ultrasonically to smartphone gyroscopes and sending Morse code signals via LEDs on network interface cards. Dubbed Gairoscope and EtherLED respectively, the two exploits are the latest in a long line of research from Guri, who has previously developed air gap exfiltration methods, including stealing data by reading the radio frequency of networking cables, using RAM buses to transmit data electromagnetically, and doing the same with power supplies.