Security News

Suspected Chinese hackers disproportionately targeted and breached government and government-linked organizations worldwide in recent attacks targeting a Barracuda Email Security Gateway zero-day, with a focus on entities across the Americas. Barracuda warned customers that the vulnerability was being exploited to breach ESG appliances on May 20, when it also patched all vulnerable devices remotely.

Thousands of Openfire XMPP servers are unpatched against a recently disclosed high-severity flaw and are susceptible to a new exploit, according to a new report from VulnCheck. "A later upgrade of the embedded web server included support for non-standard URL encoding of UTF-16 characters. The path traversal protections in place in Openfire were not updated to include protection against this new encoding."

Thousands of Openfire servers remain vulnerable to CVE-2023-32315, an actively exploited and path traversal vulnerability that allows an unauthenticated user to create new admin accounts. Still, in June, it was reported [1, 2] that the flaw was actively exploited to create admin users and upload malicious plugins on unpatched servers.

CloudNordic has told customers to consider all of their data lost following a ransomware infection that encrypted the large Danish cloud provider's servers and "Paralyzed CloudNordic completely," according to the IT outfit's online confession. While none of this is good news to organizations that have now lost all of their website and email data, CloudNordic does offer a slight silver lining: the biz doesn't believe that the criminals exfiltrated any information before encrypting the systems.
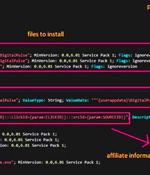
Threat actors are leveraging access to malware-infected Windows and macOS machines to deliver a proxy server application and use them as exit nodes to reroute proxy requests. According to AT&T Alien Labs, the unnamed company that offers the proxy service operates more than 400,000 proxy exit nodes, although it's not immediately clear how many of them were co-opted by malware installed on infected machines without user knowledge and interaction.

An ongoing phishing campaign has been underway since at least April 2023 that attempts to steal credentials for Zimbra Collaboration email servers worldwide. According to the ESET researchers, the attacks start with a phishing email pretending to be from an organization's admin informing users of an imminent email server update, which will result in temporary account deactivation.

A threat actor has compromised close to 2,000 thousand Citrix NetScaler servers in a massive campaign exploiting the critical-severity remote code execution tracked as CVE-2023-3519. Security researchers at cybersecurity company Fox-IT and the Dutch Institute of Vulnerability Disclosure have discovered a large-scale campaign that planted webshells on Citrix Netscaler servers vulnerable to CVE-2023-3519.

In the DOJ's blunt words, "Grabowski remains a fugitive." As you probably know, ransomware criminals typically use anonymous darkweb hosts for contact purposes when they're "Negotiating" their blackmail payoffs.

The Monti ransomware gang has returned, after a two-month break from publishing victims on their data leak site, using a new Linux locker to target VMware ESXi servers, legal, and government organizations. Researchers at Trend Micro analyzing the new encryption tool from Monti found that it has "Significant deviations from its other Linux-based predecessors."

European and U.S. law enforcement agencies have announced the dismantling of a bulletproof hosting service provider called Lolek Hosted, which cybercriminals have used to launch cyber-attacks...