Security News
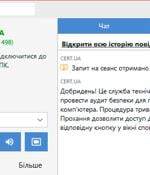
The Computer Emergency Response Team of Ukraine (CERT-UA) is warning of ongoing attempts by unknown threat actors to impersonate the cybersecurity agency by sending AnyDesk connection requests....

Attackers are impersonating the Computer Emergency Response Team of Ukraine (CERT-UA) via AnyDesk to gain access to target computers. The request (Source: CERT-UA) “Unidentified individuals are...

The FreeBSD Foundation, in partnership with the Alpha-Omega Project, has released the results of an extensive security audit of two critical FreeBSD components: the bhyve hypervisor and the...

Google Play, Android's official app store, is now tagging VPN apps with an 'independent security reviews' badge if they conducted an independent security audit of their software and platform. Starting with VPN apps, which Google considers critical for user privacy and security due to handling sensitive data, the Play Store will display the "Independent security review" badge in the Data Safety Section.

Progress Software warned customers today of newly found critical SQL injection vulnerabilities in its MOVEit Transfer managed file transfer solution that can let attackers steal information from customers' databases. "An attacker could submit a crafted payload to a MOVEit Transfer application endpoint which could result in modification and disclosure of MOVEit database content," Progress says in an advisory published today.

Hackers exploited a Level Finance smart contract vulnerability to drain 214,000 LVL tokens from the decentralized exchange and swapped them for 3,345 BNB, worth approximately $1,100,000. While Level Finance said the attack did not affect its liquidity pool and the DAO treasury, and the exploit was isolated from all other contracts, the LVL token lost roughly 50% of its value immediately after the attack was made known.

If you're a cloud service vendor, you should be prepared to answer this question from your customers: How can you prove your security and privacy practices are truly secure? An external review validates your existing security practices.

Lynis is more than just a rootkit detector, as it makes it possible to run detailed auditing of your Linux servers for numerous security issues as well as misconfigurations. I want to walk you through the process of installing Lynis and running a scan on AlmaLinux.

The US Cybersecurity and Infrastructure Security Agency has released the Ransomware Readiness Assessment, a new module for its Cyber Security Evaluation Tool. RRA is a security audit self-assessment tool for organizations that want to understand better how well they are equipped to defend against and recover from ransomware attacks targeting their information technology, operational technology, or industrial control system assets.

The US Department of the Interior spectacularly failed its latest computer security assessment, mostly for a lack of Wi-Fi defenses. The infosec experts also noted other security shortfalls, such as a lack of network segmentation that would allow intruders to casually move between systems, incomplete inventory records of wireless networks, and a reliance on pre-shared keys that could be exploited by miscreants to eavesdrop on network traffic.