Security News

Leaseweb, one of the world's largest cloud and hosting providers, notified people that it's working on restoring "Critical" systems disabled following a recent security breach.Leaseweb took down some of the impacted systems to mitigate security risks and says that its teams are now working to restore critical systems affected in this incident.

New capabilities in Google Workspace will help enterprises improve account and data security, by making unauthorized takeover of admin and user accounts and exfiltration of sensitive data more difficult. A multi-party approval request in Google Workspace Admin console.

IEEE 802.11az integrates positioning protocols to mainstream IEEE 802.11ax, while providing additional benefits such as security and authenticity, 2x to 4x improved accuracy and coverage, 10x improved power efficiency, and dramatic improvement to scalability. What is the evolutionary significance of the IEEE 802.11az standard, or Next Generation Positioning, in the context of the IEEE 802.11 series?

mWISE is unique among security conferences in its highly collaborative agenda. The 2023 lineup covers topics in cloud security, intelligence, security engineering, security operations, threats and exploits, and third-party and cyber risk management, along with a sponsor track.
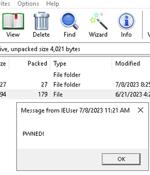
A recently patched security flaw in the popular WinRAR archiving software has been exploited as a zero-day since April 2023, new findings from Group-IB reveal. The vulnerability, cataloged as CVE-2023-38831, allows threat actors to spoof file extensions, thereby making it possible to launch malicious scripts contained within an archive that masquerades as seemingly innocuous image or text files.

The enterprise perimeter is now a massively decentralized IT landscape characterized by large-scale adoption of cloud platforms, digital services, and an increasingly tangled digital supply chain. Regulators are on the march as new threat actors emerge, exploiting increasingly sophisticated attack vectors to compromise organizations faster.

The MOVEit hack was not the same as classic ransomware attacks for which groups like Clop initially gained notoriety. Emerging digital forensic analysis from the aftermath of MOVEit suggests the hackers knew about the zero-day flaw in MOVEit as far back as 2021 when they tested it out covertly to see how much access they could get.
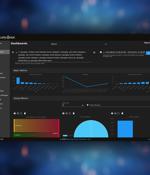
Security Onion is a free and open platform for threat hunting, enterprise security monitoring, and log management.It has been downloaded over 2 million times and is being used by security teams worldwide.

Cybercriminals employ artificial intelligence to create complex email threats like phishing and business email compromise attacks, while modern email security systems use AI to counter these attacks, according to Perception Point and Osterman Research. Cybercriminals have shown rapid adoption of AI tools to their favor with 91.1% of organizations reporting that they have already encountered email attacks that have been enhanced by AI, and 84.3% expecting that AI will continue to be utilized to circumvent existing security systems.

In the modern world it's become increasingly likely that virtual systems and IT-adjacent technologies are utilized to manage and control installed physical security devices, meaning that an effective and safe security system must be designed with input from both physical security and IT teams. In a newly converged cloud-based security system, IT staff may attempt to access and adjust physical security hardware in line with their own set of internal policies, accidentally exposing exploits or vulnerabilities that were previously covered only by physical security protocols.