Security News

A woman in the Indian city of Delhi last week found herself under "Digital arrest" - a form of scam in which victims make payments to criminals posing as law enforcement officers. Local media reported that the suspects had extorted others in a similar manner - posing as CBI officers and threatening to arrest family members of victims.

KnowBe4's quarterly phishing test report found that threat actors in Q2 often found success with emails spoofing HR departments. TechRepublic spoke with KnowBe4 Security Awareness Advocate Erich Kron about the results of the phishing tests and how to keep businesses safe from ever-evolving, generative AI-powered phishing attacks.

Cyber scams pose a significant threat to organizations of all sizes, regardless of their industry or geographic location. This guide, written by Franklin Okeke for TechRepublic Premium, digs into the nature of these scams while also highlighting the measures organizations can take to shield their employees from becoming victims.
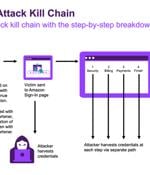
Cybersecurity researchers have discovered a novel phishing campaign that leverages Google Drawings and shortened links generated via WhatsApp to evade detection and trick users into clicking on bogus links designed to steal sensitive information. "The attackers chose a group of the best-known websites in computing to craft the threat, including Google and WhatsApp to host the attack elements, and an Amazon look-alike to harvest the victim's information," Menlo Security researcher Ashwin Vamshi said.

Two days is all it took for Interpol to recover more than $40 million worth of stolen funds in a recent business email compromise heist, the international cop shop said this week. Interpol was called in after an unidentified Singaporean commodity biz filed a police report on July 23 claiming it had been scammed out of $42.3 million four days earlier.

INTERPOL said it devised a "Global stop-payment mechanism" that helped facilitate the largest-ever recovery of funds defrauded in a business email compromise scam. The development comes after an unnamed commodity firm based in Singapore fell victim to a BEC scam in mid-July 2024.

Highlighting growth of phishing and digital scams targeting United States citizens, Bolster released a research that identified 24 separate nation-state threat actor groups attempting to exploit rising political tensions across the US to interfere with the 2024 presidential election. "We know the frequency of phishing attacks is increasing, as hackers utilize AI to execute more scams than ever before. In fact, phishing scams are being hosted in the US at a rate of nearly double, compared to 2023. The trend is only accelerating. In May alone, we logged a daily average of more than 45K malicious phishing sites," said Abhilash Garimella, VP of Research at Bolster.

The leader of a tech support fraud scheme was sentenced to seven years in prison after tricking at least 6,500 victims and generating more than $6 million. [...]
Cybersecurity researchers are warning about a new phishing campaign that targets Microsoft OneDrive users with the aim of executing a malicious PowerShell script. The cybersecurity company is tracking the "Crafty" phishing and downloader campaign under the name OneDrive Pastejacking.

CrowdStrike is alerting about an unfamiliar threat actor attempting to capitalize on the Falcon Sensor update fiasco to distribute dubious installers targeting German customers as part of a highly targeted campaign. The cybersecurity company said it identified what it described as an unattributed spear-phishing attempt on July 24, 2024, distributing an inauthentic CrowdStrike Crash Reporter installer via a website impersonating an unnamed German entity.