Security News

Security researchers have disclosed a security vulnerability in the VirusTotal platform that could have been potentially weaponized to achieve remote code execution. The flaw, now patched, made it possible to "Execute commands remotely within VirusTotal platform and gain access to its various scans capabilities," Cysource researchers Shai Alfasi and Marlon Fabiano da Silva said in a report exclusively shared with The Hacker News.

A proof-of-concept code demonstrating a newly disclosed digital signature bypass vulnerability in Java has been shared online. The high-severity flaw in question, CVE-2022-21449, impacts the following version of Java SE and Oracle GraalVM Enterprise Edition -.

Details have emerged about a now-patched security vulnerability in the Snort intrusion detection and prevention system that could trigger a denial-of-service condition and render it powerless against malicious traffic. Tracked as CVE-2022-20685, the vulnerability is rated 7.5 for severity and resides in the Modbus preprocessor of the Snort detection engine.

An 18-month-long analysis of the PYSA ransomware operation has revealed that the cybercrime cartel followed a five-stage software development cycle from August 2020, with the malware authors prioritizing features to improve the efficiency of its workflows. PYSA, short for "Protect Your System, Amigo" and a successor of the Mespinoza ransomware, was first observed in December 2019 and has emerged as the third most prevalent ransomware strain detected during the fourth quarter of 2021.

Cybersecurity researchers are warning of two different information-stealing malware, named FFDroider and Lightning Stealer, that are capable of siphoning data and launching further attacks. FFDroider is distributed through cracked versions of installers and freeware with the primary objective of stealing cookies and credentials associated with popular social media and e-commerce platforms and using the plundered data to login into the accounts and capture other personal account-related information.

Cybersecurity researchers have uncovered further links between BlackCat and BlackMatter ransomware families, the former of which emerged as a replacement following international scrutiny last year. "At least some members of the new BlackCat group have links to the BlackMatter group, because they modified and reused a custom exfiltration tool and which has only been observed in BlackMatter activity," Kaspersky researchers said in a new analysis.
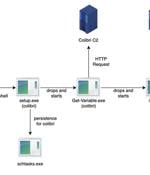
Cybersecurity researchers have detailed a "Simple but efficient" persistence mechanism adopted by a relatively nascent malware loader called Colibri, which has been observed deploying a Windows information stealer known as Vidar as part of a new campaign. "The attack starts with a malicious Word document deploying a Colibri bot that then delivers the Vidar Stealer," Malwarebytes Labs said in an analysis.
A Chinese state-backed advanced persistent threat group known for singling out Japanese entities has been attributed to a new long-running espionage campaign targeting new geographies, suggesting a "Widening" of the threat actor's targeting. "Victims in this Cicada campaign include government, legal, religious, and non-governmental organizations in multiple countries around the world, including in Europe, Asia, and North America," researchers from the Symantec Threat Hunter Team, part of Broadcom Software, said in a report shared with The Hacker News.

An Android spyware application has been spotted masquerading as a "Process Manager" service to stealthily siphon sensitive information stored in the infected devices. "When the application is run, a warning appears about the permissions granted to the application," Lab52 researchers said.
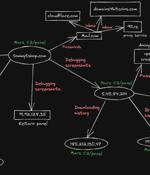
A nascent information stealer called Mars has been observed in campaigns that take advantage of cracked versions of the malware to steal information stored in web browsers and cryptocurrency wallets. "Mars Stealer is being distributed via social engineering techniques, malspam campaigns, malicious software cracks, and keygens," Morphisec malware researcher Arnold Osipov said in a report published Tuesday.