Security News

The prolific SideWinder group has been attributed as the nation-state actor behind attempted attacks against 61 entities in Afghanistan, Bhutan, Myanmar, Nepal, and Sri Lanka between June and November 2021. The group has been linked to no less than 1,000 attacks against government organizations in the Asia-Pacific region since April 2020, according to a report from the Russian cybersecurity firm early last year.
Security researchers have disclosed two new vulnerabilities affecting Schneider Electric Modicon programmable logic controllers that could allow for authentication bypass and remote code execution. The flaws, tracked as CVE-2022-45788 and CVE-2022-45789, are part of a broader collection of security defects tracked by Forescout as OT:ICEFALL. Successful exploitation of the bugs could enable an adversary to execute unauthorized code, denial-of-service, or disclosure of sensitive information.

In it, a pig butchering romance scammer targets her next victim: Sophos's lead threat researcher. "I was approached by multiple, separate scam operations personally, each running different variations on pig butchering," Sophos's principal threat researcher Sean Gallagher wrote in a blog post today about one of these attempts.

Four different rogue packages in the Python Package Index have been found to carry out a number of malicious actions, including dropping malware, deleting the netstat utility, and manipulating the SSH authorized keys file. "Most of these packages had well thought out names, to purposely confuse people," Security researcher and journalist Ax Sharma said.

Toyota's Global Supplier Preparation Information Management System was breached by a security researcher who responsibly reported the issue to the company. The issues were responsibly disclosed to Toyota on November 3, 2022, and the Japanese car maker confirmed they had been fixed by November 23, 2022.

Cybersecurity researchers have disclosed details of two security flaws in the open source ImageMagick software that could potentially lead to a denial-of-service and information disclosure. The two issues, which were identified by Latin American cybersecurity firm Metabase Q in version 7.1.0-49, were addressed in ImageMagick version 7.1.0-52, released in November 2022.

A shellcode-based packer dubbed TrickGate has been successfully operating without attracting notice for over six years, while enabling threat actors to deploy a wide range of malware such as TrickBot, Emotet, AZORult, Agent Tesla, FormBook, Cerber, Maze, and REvil over the years. "TrickGate managed to stay under the radar for years because it is transformative - it undergoes changes periodically," Check Point Research's Arie Olshtein said, calling it a "Master of disguises."

Security researchers with Horizon3's Attack Team will release an exploit targeting a vulnerability chain next week for gaining remote code execution on unpatched VMware vRealize Log Insight appliances. Now known as VMware Aria Operations for Logs, vRealize Log Insight makes it easier for VMware admins to analyze and manage terabytes of infrastructure and application logs.
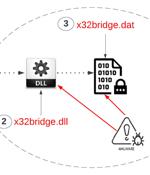
Cybersecurity researchers have uncovered a PlugX sample that employs sneaky methods to infect attached removable USB media devices in order to propagate the malware to additional systems. "This PlugX variant is wormable and infects USB devices in such a way that it conceals itself from the Windows operating file system," Palo Alto Networks Unit 42 researchers Mike Harbison and Jen Miller-Osborn said.
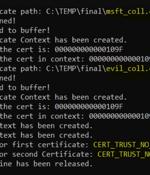
Proof-of-concept (Poc) code has been released for a now-patched high-severity security flaw in the Windows CryptoAPI that the U.S. National Security Agency (NSA) and the U.K. National Cyber...