Security News

This Remote Access Checklist from TechRepublic Premium should be used to ensure all employees have the requisite items, accounts, access and instructions needed for remote work. Resource Details Download for $9 or Access all downloads for $299/yr*.
A new remote access trojan called QwixxRAT is being advertised for sale by its threat actor through Telegram and Discord platforms. "Once installed on the victim's Windows platform machines, the RAT stealthily collects sensitive data, which is then sent to the attacker's Telegram bot, providing them with unauthorized access to the victim's sensitive information," Uptycs said in a new report published today.

"The report shows 92% of survey respondents recognize the importance of adopting a zero trust architecture; however, it is concerning to see many organizations are still using a VPN for remote employee and third-party access, inadvertently providing a juicy attack surface for threat actors," said Deepen Desai, Global CISO and Head of Security Research, Zscaler. "Legacy firewall and VPN vendors are spinning virtual VPNs in the cloud and claiming that it is zero trust, and they go the extra length to hide the word"VPN". Customers need to ask the right questions to make sure that they are not getting a false sense of security with these virtualized legacy offerings in the cloud. In order to safeguard against evolving ransomware attacks, it is critical for organizations to eliminate the use of VPNs, prioritize user-to-app segmentation, and implement an in-line contextual data loss prevention engine with full TLS inspection," added Desai.

Mitiga researchers have documented a new post-exploitation technique attackers can use to gain persistent remote access to AWS Elastic Compute Cloud (EC2) instances (virtual servers), as well as...
Cybersecurity researchers have discovered a new post-exploitation technique in Amazon Web Services that allows the AWS Systems Manager Agent to be run as a remote access trojan on Windows and Linux environments. "The SSM agent, a legitimate tool used by admins to manage their instances, can be re-purposed by an attacker who has achieved high privilege access on an endpoint with SSM agent installed, to carry out malicious activities on an ongoing basis," Mitiga researchers Ariel Szarf and Or Aspir said in a report shared with The Hacker News.
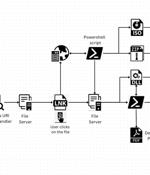
A legitimate Windows search feature is being exploited by malicious actors to download arbitrary payloads from remote servers and compromise targeted systems with remote access trojans such as AsyncRAT and Remcos RAT. The novel attack technique, per Trellix, takes advantage of the "Search-ms:" URI protocol handler, which offers the ability for applications and HTML links to launch custom local searches on a device, and the "Search:" application protocol, a mechanism for calling the desktop search application on Windows. It's worth noting that clicking on the link also generates a warning "Open Windows Explorer?," approving which "The search results of remotely hosted malicious shortcut files are displayed in Windows Explorer disguised as PDFs or other trusted icons, just like local search results," the researchers explained.

TechRepublic Premium Checklist: How to Create a Team Charter A good team charter should define the purpose of a team, how work will get done and the expected outcomes. Often, a team charter is described as a "Roadmap" for the team and its sponsors.
A new phishing campaign codenamed MULTI#STORM has set its sights on India and the U.S. by leveraging JavaScript files to deliver remote access trojans on compromised systems. The multi-stage attack chain commences when an email recipient clicks the embedded link pointing to a password-protected ZIP file hosted on Microsoft OneDrive with the password "12345."
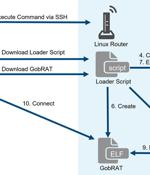
Linux routers in Japan are the target of a new Golang remote access trojan called GobRAT. "Initially, the attacker targets a router whose WEBUI is open to the public, executes scripts possibly by using vulnerabilities, and finally infects the GobRAT," the JPCERT Coordination Center said in a report published today. The compromise of an internet-exposed router is followed by the deployment of a loader script that acts as a conduit for delivering GobRAT, which, when launched, masquerades as the Apache daemon process to evade detection.

In an effort to solve the access-related challenges facing OT and critical infrastructure operators, the team at Cyolo built a zero-trust access platform designed to meet the unique safety, security, and uptime requirements of OT and industrial control systems environments. Let's look under the hood: #. The Cyolo solution is a high-powered combination of Zero Trust Network Access, Identity Provider, and Privileged Access Management.