Security News

The OAS platform is a widely used data connectivity solution that unites industrial devices, SCADA systems, IoTs, network points, custom applications, custom APIs, and databases under a holistic system. According to a report by Cisco Talos, OAS platform version 16.00.0112 and below is vulnerable to a range of high and critical severity bugs that create the potential for damaging attacks.

Zoom patched a medium-severity flaw, advising Windows, macOS, iOS and Android users to update their client software to version 5.10.0. The Google Project Zero security researcher Ivan Fratric noted in a report that an attacker can exploit a victim's machine over a zoom chat.

The U.S. Cybersecurity and Infrastructure Security Agency on Monday added two security flaws, including the recently disclosed remote code execution bug affecting Zyxel firewalls, to its Known Exploited Vulnerabilities Catalog, citing evidence of active exploitation. Tracked as CVE-2022-30525, the vulnerability is rated 9.8 for severity and relates to a command injection flaw in select versions of the Zyxel firewall that could enable an unauthenticated adversary to execute arbitrary commands on the underlying operating system.

Researchers uncover URL spoofing flaws on Zoom, Box, Google DocsResearchers have discovered several URL spoofing bugs in Box, Zoom and Google Docs that would allow phishers to generate links to malicious content and make it look like it's hosted by an organization's SaaS account. A 10-point plan to improve the security of open source softwareThe Linux Foundation and the Open Source Software Security Foundation, with input provided by executives from 37 companies and many U.S. government leaders, delivered a 10-point plan to broadly address open source and software supply chain security, by securing open source security production, improving vulnerability discovery and remediation, and shortening the patching response time of the ecosystem.

Threat analysts who discovered a vulnerability affecting multiple Zyxel products report that the network equipment company fixed it via a silent update pushed out two weeks ago. More specifically, security researchers at Rapid7 found the flaw, which is now tracked as CVE-2022-30525, and disclosed it to Zyxel on April 13, 2022.

Microsoft on Monday disclosed that it mitigated a security flaw affecting Azure Synapse and Azure Data Factory that, if successfully exploited, could result in remote code execution. "The vulnerability was specific to the third-party Open Database Connectivity driver used to connect to Amazon Redshift in Azure Synapse pipelines and Azure Data Factory Integration Runtime and did not impact Azure Synapse as a whole," the company said.
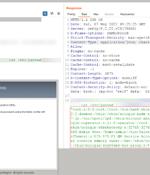
Days after F5 released patches for a critical remote code execution vulnerability affecting its BIG-IP family of products, security researchers are warning that they were able to create an exploit for the shortcoming. The critical security vulnerability impacts the following versions of BIG-IP products -.

Microsoft has released security updates to address a security flaw affecting Azure Synapse and Azure Data Factory pipelines that could let attackers execute remote commands across Integration Runtime infrastructure.The Integration Runtime compute infrastructure is used by Azure Synapse and Azure Data Factory pipelines to provide data integration capabilities across network environments package execution).

Researchers have developed PoC exploits for CVE-2022-1388, a critical remote code execution bug affecting F5 BIG-IP multi-purpose networking devices/modules. We have reproduced the fresh CVE-2022-1388 in F5's BIG-IP. Successful exploitation could lead to RCE from an unauthenticated user.

F5 has issued a security advisory warning about a flaw that may allow unauthenticated attackers with network access to execute arbitrary system commands, perform file actions, and disable services on BIG-IP. The vulnerability is tracked as CVE-2022-1388 and has a CVSS v3 severity rating of 9.8, categorized as critical. According to F5's security advisory, the flaw lies in the iControl REST component and allows a malicious actor to send undisclosed requests to bypass the iControl REST authentication in BIG-IP. Due to the severity of the vulnerability and the widespread deployment of BIG-IP products in critical environments, CISA has also issued an alert today.