Security News

A joint police operation between the Australian Federal Police and the FBI has led to the arrest and charging of two individuals who are believed to be behind the development and distribution of the "Firebird" remote access trojan, later rebranded as "Hive.". The Australian Federal Police alleges that the Australian developed and sold the RAT on a dedicated hacking forum, enabling other users who paid for the tool to remotely access victims' computers and perform unauthorized activity.
The threat actor known as TA558 has been attributed to a new massive phishing campaign that targets a wide range of sectors in Latin America with the goal of deploying Venom RAT. The attacks...

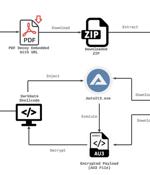
Employees at US-based organizations are being targeted with emails delivering NetSupport RAT malware via "Nuanced" exploitation and by using an advanced detection evasion method. The phishing emails prompts recipients to download an attached Office Word file to view their "Monthly salary report".

Multiple threat actors are exploiting the recently disclosed security flaws in JetBrains TeamCity software to deploy ransomware, cryptocurrency miners, Cobalt Strike beacons, and a Golang-based...
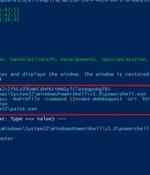
A new phishing campaign is targeting U.S. organizations with the intent to deploy a remote access trojan called NetSupport RAT. Israeli cybersecurity company Perception Point is tracking the...

A financially motivated threat actor called Magnet Goblin is swiftly adopting one-day security vulnerabilities into its arsenal in order to opportunistically breach edge devices and public-facing...

An "intricately designed" remote access trojan (RAT) called Xeno RAT has been made available on GitHub, making it available to other actors at no extra cost. Written in C# and compatible with...

A hacking group tracked as 'UAC-0184' was observed utilizing steganographic image files to deliver the Remcos remote access trojan onto the systems of a Ukrainian entity operating in Finland. Steganography is a well-documented but rarely seen tactic that involves encoding malicious code into the pixel data of images to evade detection by solutions using signature-based rules.
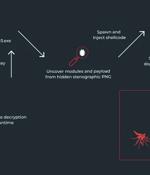
Ukrainian entities based in Finland have been targeted as part of a malicious campaign distributing a commercial remote access trojan known as Remcos RAT using a malware loader called IDAT Loader....

An installer for a tool likely used by the Russian Consular Department of the Ministry of Foreign Affairs (MID) has been backdoored to deliver a remote access trojan called Konni RAT (aka UpDog)....